mirror of
https://github.com/astaxie/beego.git
synced 2025-09-16 10:32:10 +00:00
update mod
This commit is contained in:
27
vendor/github.com/casbin/casbin/.gitignore
generated
vendored
Normal file
27
vendor/github.com/casbin/casbin/.gitignore
generated
vendored
Normal file
@@ -0,0 +1,27 @@
|
||||
# Compiled Object files, Static and Dynamic libs (Shared Objects)
|
||||
*.o
|
||||
*.a
|
||||
*.so
|
||||
|
||||
# Folders
|
||||
_obj
|
||||
_test
|
||||
|
||||
# Architecture specific extensions/prefixes
|
||||
*.[568vq]
|
||||
[568vq].out
|
||||
|
||||
*.cgo1.go
|
||||
*.cgo2.c
|
||||
_cgo_defun.c
|
||||
_cgo_gotypes.go
|
||||
_cgo_export.*
|
||||
|
||||
_testmain.go
|
||||
|
||||
*.exe
|
||||
*.test
|
||||
*.prof
|
||||
|
||||
.idea/
|
||||
*.iml
|
||||
12
vendor/github.com/casbin/casbin/.travis.yml
generated
vendored
Normal file
12
vendor/github.com/casbin/casbin/.travis.yml
generated
vendored
Normal file
@@ -0,0 +1,12 @@
|
||||
language: go
|
||||
|
||||
sudo: false
|
||||
|
||||
go:
|
||||
- tip
|
||||
|
||||
before_install:
|
||||
- go get github.com/mattn/goveralls
|
||||
|
||||
script:
|
||||
- $HOME/gopath/bin/goveralls -service=travis-ci
|
||||
201
vendor/github.com/casbin/casbin/LICENSE
generated
vendored
Normal file
201
vendor/github.com/casbin/casbin/LICENSE
generated
vendored
Normal file
@@ -0,0 +1,201 @@
|
||||
Apache License
|
||||
Version 2.0, January 2004
|
||||
http://www.apache.org/licenses/
|
||||
|
||||
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
|
||||
|
||||
1. Definitions.
|
||||
|
||||
"License" shall mean the terms and conditions for use, reproduction,
|
||||
and distribution as defined by Sections 1 through 9 of this document.
|
||||
|
||||
"Licensor" shall mean the copyright owner or entity authorized by
|
||||
the copyright owner that is granting the License.
|
||||
|
||||
"Legal Entity" shall mean the union of the acting entity and all
|
||||
other entities that control, are controlled by, or are under common
|
||||
control with that entity. For the purposes of this definition,
|
||||
"control" means (i) the power, direct or indirect, to cause the
|
||||
direction or management of such entity, whether by contract or
|
||||
otherwise, or (ii) ownership of fifty percent (50%) or more of the
|
||||
outstanding shares, or (iii) beneficial ownership of such entity.
|
||||
|
||||
"You" (or "Your") shall mean an individual or Legal Entity
|
||||
exercising permissions granted by this License.
|
||||
|
||||
"Source" form shall mean the preferred form for making modifications,
|
||||
including but not limited to software source code, documentation
|
||||
source, and configuration files.
|
||||
|
||||
"Object" form shall mean any form resulting from mechanical
|
||||
transformation or translation of a Source form, including but
|
||||
not limited to compiled object code, generated documentation,
|
||||
and conversions to other media types.
|
||||
|
||||
"Work" shall mean the work of authorship, whether in Source or
|
||||
Object form, made available under the License, as indicated by a
|
||||
copyright notice that is included in or attached to the work
|
||||
(an example is provided in the Appendix below).
|
||||
|
||||
"Derivative Works" shall mean any work, whether in Source or Object
|
||||
form, that is based on (or derived from) the Work and for which the
|
||||
editorial revisions, annotations, elaborations, or other modifications
|
||||
represent, as a whole, an original work of authorship. For the purposes
|
||||
of this License, Derivative Works shall not include works that remain
|
||||
separable from, or merely link (or bind by name) to the interfaces of,
|
||||
the Work and Derivative Works thereof.
|
||||
|
||||
"Contribution" shall mean any work of authorship, including
|
||||
the original version of the Work and any modifications or additions
|
||||
to that Work or Derivative Works thereof, that is intentionally
|
||||
submitted to Licensor for inclusion in the Work by the copyright owner
|
||||
or by an individual or Legal Entity authorized to submit on behalf of
|
||||
the copyright owner. For the purposes of this definition, "submitted"
|
||||
means any form of electronic, verbal, or written communication sent
|
||||
to the Licensor or its representatives, including but not limited to
|
||||
communication on electronic mailing lists, source code control systems,
|
||||
and issue tracking systems that are managed by, or on behalf of, the
|
||||
Licensor for the purpose of discussing and improving the Work, but
|
||||
excluding communication that is conspicuously marked or otherwise
|
||||
designated in writing by the copyright owner as "Not a Contribution."
|
||||
|
||||
"Contributor" shall mean Licensor and any individual or Legal Entity
|
||||
on behalf of whom a Contribution has been received by Licensor and
|
||||
subsequently incorporated within the Work.
|
||||
|
||||
2. Grant of Copyright License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
copyright license to reproduce, prepare Derivative Works of,
|
||||
publicly display, publicly perform, sublicense, and distribute the
|
||||
Work and such Derivative Works in Source or Object form.
|
||||
|
||||
3. Grant of Patent License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
(except as stated in this section) patent license to make, have made,
|
||||
use, offer to sell, sell, import, and otherwise transfer the Work,
|
||||
where such license applies only to those patent claims licensable
|
||||
by such Contributor that are necessarily infringed by their
|
||||
Contribution(s) alone or by combination of their Contribution(s)
|
||||
with the Work to which such Contribution(s) was submitted. If You
|
||||
institute patent litigation against any entity (including a
|
||||
cross-claim or counterclaim in a lawsuit) alleging that the Work
|
||||
or a Contribution incorporated within the Work constitutes direct
|
||||
or contributory patent infringement, then any patent licenses
|
||||
granted to You under this License for that Work shall terminate
|
||||
as of the date such litigation is filed.
|
||||
|
||||
4. Redistribution. You may reproduce and distribute copies of the
|
||||
Work or Derivative Works thereof in any medium, with or without
|
||||
modifications, and in Source or Object form, provided that You
|
||||
meet the following conditions:
|
||||
|
||||
(a) You must give any other recipients of the Work or
|
||||
Derivative Works a copy of this License; and
|
||||
|
||||
(b) You must cause any modified files to carry prominent notices
|
||||
stating that You changed the files; and
|
||||
|
||||
(c) You must retain, in the Source form of any Derivative Works
|
||||
that You distribute, all copyright, patent, trademark, and
|
||||
attribution notices from the Source form of the Work,
|
||||
excluding those notices that do not pertain to any part of
|
||||
the Derivative Works; and
|
||||
|
||||
(d) If the Work includes a "NOTICE" text file as part of its
|
||||
distribution, then any Derivative Works that You distribute must
|
||||
include a readable copy of the attribution notices contained
|
||||
within such NOTICE file, excluding those notices that do not
|
||||
pertain to any part of the Derivative Works, in at least one
|
||||
of the following places: within a NOTICE text file distributed
|
||||
as part of the Derivative Works; within the Source form or
|
||||
documentation, if provided along with the Derivative Works; or,
|
||||
within a display generated by the Derivative Works, if and
|
||||
wherever such third-party notices normally appear. The contents
|
||||
of the NOTICE file are for informational purposes only and
|
||||
do not modify the License. You may add Your own attribution
|
||||
notices within Derivative Works that You distribute, alongside
|
||||
or as an addendum to the NOTICE text from the Work, provided
|
||||
that such additional attribution notices cannot be construed
|
||||
as modifying the License.
|
||||
|
||||
You may add Your own copyright statement to Your modifications and
|
||||
may provide additional or different license terms and conditions
|
||||
for use, reproduction, or distribution of Your modifications, or
|
||||
for any such Derivative Works as a whole, provided Your use,
|
||||
reproduction, and distribution of the Work otherwise complies with
|
||||
the conditions stated in this License.
|
||||
|
||||
5. Submission of Contributions. Unless You explicitly state otherwise,
|
||||
any Contribution intentionally submitted for inclusion in the Work
|
||||
by You to the Licensor shall be under the terms and conditions of
|
||||
this License, without any additional terms or conditions.
|
||||
Notwithstanding the above, nothing herein shall supersede or modify
|
||||
the terms of any separate license agreement you may have executed
|
||||
with Licensor regarding such Contributions.
|
||||
|
||||
6. Trademarks. This License does not grant permission to use the trade
|
||||
names, trademarks, service marks, or product names of the Licensor,
|
||||
except as required for reasonable and customary use in describing the
|
||||
origin of the Work and reproducing the content of the NOTICE file.
|
||||
|
||||
7. Disclaimer of Warranty. Unless required by applicable law or
|
||||
agreed to in writing, Licensor provides the Work (and each
|
||||
Contributor provides its Contributions) on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
|
||||
implied, including, without limitation, any warranties or conditions
|
||||
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
|
||||
PARTICULAR PURPOSE. You are solely responsible for determining the
|
||||
appropriateness of using or redistributing the Work and assume any
|
||||
risks associated with Your exercise of permissions under this License.
|
||||
|
||||
8. Limitation of Liability. In no event and under no legal theory,
|
||||
whether in tort (including negligence), contract, or otherwise,
|
||||
unless required by applicable law (such as deliberate and grossly
|
||||
negligent acts) or agreed to in writing, shall any Contributor be
|
||||
liable to You for damages, including any direct, indirect, special,
|
||||
incidental, or consequential damages of any character arising as a
|
||||
result of this License or out of the use or inability to use the
|
||||
Work (including but not limited to damages for loss of goodwill,
|
||||
work stoppage, computer failure or malfunction, or any and all
|
||||
other commercial damages or losses), even if such Contributor
|
||||
has been advised of the possibility of such damages.
|
||||
|
||||
9. Accepting Warranty or Additional Liability. While redistributing
|
||||
the Work or Derivative Works thereof, You may choose to offer,
|
||||
and charge a fee for, acceptance of support, warranty, indemnity,
|
||||
or other liability obligations and/or rights consistent with this
|
||||
License. However, in accepting such obligations, You may act only
|
||||
on Your own behalf and on Your sole responsibility, not on behalf
|
||||
of any other Contributor, and only if You agree to indemnify,
|
||||
defend, and hold each Contributor harmless for any liability
|
||||
incurred by, or claims asserted against, such Contributor by reason
|
||||
of your accepting any such warranty or additional liability.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
APPENDIX: How to apply the Apache License to your work.
|
||||
|
||||
To apply the Apache License to your work, attach the following
|
||||
boilerplate notice, with the fields enclosed by brackets "{}"
|
||||
replaced with your own identifying information. (Don't include
|
||||
the brackets!) The text should be enclosed in the appropriate
|
||||
comment syntax for the file format. We also recommend that a
|
||||
file or class name and description of purpose be included on the
|
||||
same "printed page" as the copyright notice for easier
|
||||
identification within third-party archives.
|
||||
|
||||
Copyright {yyyy} {name of copyright owner}
|
||||
|
||||
Licensed under the Apache License, Version 2.0 (the "License");
|
||||
you may not use this file except in compliance with the License.
|
||||
You may obtain a copy of the License at
|
||||
|
||||
http://www.apache.org/licenses/LICENSE-2.0
|
||||
|
||||
Unless required by applicable law or agreed to in writing, software
|
||||
distributed under the License is distributed on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
See the License for the specific language governing permissions and
|
||||
limitations under the License.
|
||||
366
vendor/github.com/casbin/casbin/README.md
generated
vendored
Normal file
366
vendor/github.com/casbin/casbin/README.md
generated
vendored
Normal file
@@ -0,0 +1,366 @@
|
||||
Casbin
|
||||
====
|
||||
|
||||
[](https://goreportcard.com/report/github.com/casbin/casbin)
|
||||
[](https://travis-ci.org/casbin/casbin)
|
||||
[](https://coveralls.io/github/casbin/casbin?branch=master)
|
||||
[](https://godoc.org/github.com/casbin/casbin)
|
||||
[](https://github.com/casbin/casbin/releases/latest)
|
||||
[](https://gitter.im/casbin/lobby)
|
||||
[](http://www.patreon.com/yangluo)
|
||||
[](https://sourcegraph.com/github.com/casbin/casbin?badge)
|
||||
|
||||
**News**: still worry about how to write the correct Casbin policy? ``Casbin online editor`` is coming to help! Try it at: http://casbin.org/editor/
|
||||
|
||||

|
||||
|
||||
Casbin is a powerful and efficient open-source access control library for Golang projects. It provides support for enforcing authorization based on various [access control models](https://en.wikipedia.org/wiki/Computer_security_model).
|
||||
|
||||
## All the languages supported by Casbin:
|
||||
|
||||
- Golang: [Casbin](https://github.com/casbin/casbin) (production-ready)
|
||||
- Java: [jCasbin](https://github.com/casbin/jcasbin) (production-ready)
|
||||
- PHP: [PHP-Casbin](https://github.com/sstutz/php-casbin) (experimental)
|
||||
- Node.js: [node-casbin](https://github.com/casbin/node-casbin) (WIP)
|
||||
- C++: xCasbin (WIP)
|
||||
|
||||
## Table of contents
|
||||
|
||||
- [Supported models](#supported-models)
|
||||
- [How it works?](#how-it-works)
|
||||
- [Features](#features)
|
||||
- [Installation](#installation)
|
||||
- [Documentation](#documentation)
|
||||
- [Online editor](#online-editor)
|
||||
- [Tutorials](#tutorials)
|
||||
- [Get started](#get-started)
|
||||
- [Policy management](#policy-management)
|
||||
- [Policy persistence](#policy-persistence)
|
||||
- [Policy consistence between multiple nodes](#policy-consistence-between-multiple-nodes)
|
||||
- [Role manager](#role-manager)
|
||||
- [Multi-threading](#multi-threading)
|
||||
- [Benchmarks](#benchmarks)
|
||||
- [Examples](#examples)
|
||||
- [How to use Casbin as a service?](#how-to-use-casbin-as-a-service)
|
||||
- [Our adopters](#our-adopters)
|
||||
|
||||
## Supported models
|
||||
|
||||
1. [**ACL (Access Control List)**](https://en.wikipedia.org/wiki/Access_control_list)
|
||||
2. **ACL with [superuser](https://en.wikipedia.org/wiki/Superuser)**
|
||||
3. **ACL without users**: especially useful for systems that don't have authentication or user log-ins.
|
||||
3. **ACL without resources**: some scenarios may target for a type of resources instead of an individual resource by using permissions like ``write-article``, ``read-log``. It doesn't control the access to a specific article or log.
|
||||
4. **[RBAC (Role-Based Access Control)](https://en.wikipedia.org/wiki/Role-based_access_control)**
|
||||
5. **RBAC with resource roles**: both users and resources can have roles (or groups) at the same time.
|
||||
6. **RBAC with domains/tenants**: users can have different role sets for different domains/tenants.
|
||||
7. **[ABAC (Attribute-Based Access Control)](https://en.wikipedia.org/wiki/Attribute-Based_Access_Control)**: syntax sugar like ``resource.Owner`` can be used to get the attribute for a resource.
|
||||
8. **[RESTful](https://en.wikipedia.org/wiki/Representational_state_transfer)**: supports paths like ``/res/*``, ``/res/:id`` and HTTP methods like ``GET``, ``POST``, ``PUT``, ``DELETE``.
|
||||
9. **Deny-override**: both allow and deny authorizations are supported, deny overrides the allow.
|
||||
10. **Priority**: the policy rules can be prioritized like firewall rules.
|
||||
|
||||
## How it works?
|
||||
|
||||
In Casbin, an access control model is abstracted into a CONF file based on the **PERM metamodel (Policy, Effect, Request, Matchers)**. So switching or upgrading the authorization mechanism for a project is just as simple as modifying a configuration. You can customize your own access control model by combining the available models. For example, you can get RBAC roles and ABAC attributes together inside one model and share one set of policy rules.
|
||||
|
||||
The most basic and simplest model in Casbin is ACL. ACL's model CONF is:
|
||||
|
||||
```ini
|
||||
# Request definition
|
||||
[request_definition]
|
||||
r = sub, obj, act
|
||||
|
||||
# Policy definition
|
||||
[policy_definition]
|
||||
p = sub, obj, act
|
||||
|
||||
# Policy effect
|
||||
[policy_effect]
|
||||
e = some(where (p.eft == allow))
|
||||
|
||||
# Matchers
|
||||
[matchers]
|
||||
m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
|
||||
|
||||
# We also support multi-line mode by appending '\' in the end:
|
||||
# m = r.sub == p.sub && r.obj == p.obj \
|
||||
# && r.act == p.act
|
||||
```
|
||||
|
||||
An example policy for ACL model is like:
|
||||
|
||||
```
|
||||
p, alice, data1, read
|
||||
p, bob, data2, write
|
||||
```
|
||||
|
||||
It means:
|
||||
|
||||
- alice can read data1
|
||||
- bob can write data2
|
||||
|
||||
## Features
|
||||
|
||||
What Casbin does:
|
||||
|
||||
1. enforce the policy in the classic ``{subject, object, action}`` form or a customized form as you defined, both allow and deny authorizations are supported.
|
||||
2. handle the storage of the access control model and its policy.
|
||||
3. manage the role-user mappings and role-role mappings (aka role hierarchy in RBAC).
|
||||
4. support built-in superuser like ``root`` or ``administrator``. A superuser can do anything without explict permissions.
|
||||
5. multiple built-in operators to support the rule matching. For example, ``keyMatch`` can map a resource key ``/foo/bar`` to the pattern ``/foo*``.
|
||||
|
||||
What Casbin does NOT do:
|
||||
|
||||
1. authentication (aka verify ``username`` and ``password`` when a user logs in)
|
||||
2. manage the list of users or roles. I believe it's more convenient for the project itself to manage these entities. Users usually have their passwords, and Casbin is not designed as a password container. However, Casbin stores the user-role mapping for the RBAC scenario.
|
||||
|
||||
## Installation
|
||||
|
||||
```
|
||||
go get github.com/casbin/casbin
|
||||
```
|
||||
|
||||
## Documentation
|
||||
|
||||
For documentation, please see: [Our Wiki](https://github.com/casbin/casbin/wiki)
|
||||
|
||||
## Online editor
|
||||
|
||||
You can also use the online editor (http://casbin.org/editor/) to write your Casbin model and policy in your web browser. It provides functionality such as ``syntax highlighting`` and ``code completion``, just like an IDE for a programming language.
|
||||
|
||||
## Tutorials
|
||||
|
||||
- [Basic Role-Based HTTP Authorization in Go with Casbin](https://zupzup.org/casbin-http-role-auth) (or [Chinese translation](https://studygolang.com/articles/12323))
|
||||
- [Policy enforcements on Kubernetes with Banzai Cloud's Pipeline and Casbin](https://banzaicloud.com/blog/policy-enforcement-k8s/)
|
||||
- [Using Casbin with Beego: 1. Get started and test (in Chinese)](https://blog.csdn.net/hotqin888/article/details/78460385)
|
||||
- [Using Casbin with Beego: 2. Policy storage (in Chinese)](https://blog.csdn.net/hotqin888/article/details/78571240)
|
||||
- [Using Casbin with Beego: 3. Policy query (in Chinese)](https://blog.csdn.net/hotqin888/article/details/78992250)
|
||||
- [Using Casbin with Beego: 4. Policy update (in Chinese)](https://blog.csdn.net/hotqin888/article/details/80032538)
|
||||
|
||||
## Get started
|
||||
|
||||
1. New a Casbin enforcer with a model file and a policy file:
|
||||
|
||||
```go
|
||||
e := casbin.NewEnforcer("path/to/model.conf", "path/to/policy.csv")
|
||||
```
|
||||
|
||||
Note: you can also initialize an enforcer with policy in DB instead of file, see [Persistence](#persistence) section for details.
|
||||
|
||||
2. Add an enforcement hook into your code right before the access happens:
|
||||
|
||||
```go
|
||||
sub := "alice" // the user that wants to access a resource.
|
||||
obj := "data1" // the resource that is going to be accessed.
|
||||
act := "read" // the operation that the user performs on the resource.
|
||||
|
||||
if e.Enforce(sub, obj, act) == true {
|
||||
// permit alice to read data1
|
||||
} else {
|
||||
// deny the request, show an error
|
||||
}
|
||||
```
|
||||
|
||||
3. Besides the static policy file, Casbin also provides API for permission management at run-time. For example, You can get all the roles assigned to a user as below:
|
||||
|
||||
```go
|
||||
roles := e.GetRoles("alice")
|
||||
```
|
||||
|
||||
See [Policy management APIs](#policy-management) for more usage.
|
||||
|
||||
4. Please refer to the ``_test.go`` files for more usage.
|
||||
|
||||
## Policy management
|
||||
|
||||
Casbin provides two sets of APIs to manage permissions:
|
||||
|
||||
- [Management API](https://github.com/casbin/casbin/blob/master/management_api.go): the primitive API that provides full support for Casbin policy management. See [here](https://github.com/casbin/casbin/blob/master/management_api_test.go) for examples.
|
||||
- [RBAC API](https://github.com/casbin/casbin/blob/master/rbac_api.go): a more friendly API for RBAC. This API is a subset of Management API. The RBAC users could use this API to simplify the code. See [here](https://github.com/casbin/casbin/blob/master/rbac_api_test.go) for examples.
|
||||
|
||||
We also provide a web-based UI for model management and policy management:
|
||||
|
||||
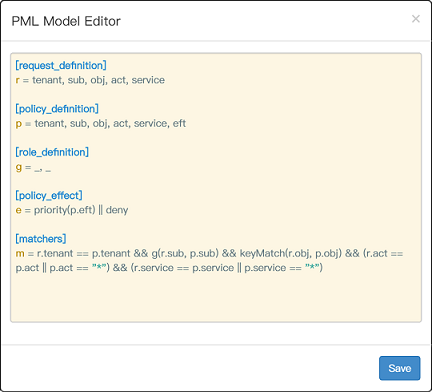
|
||||
|
||||
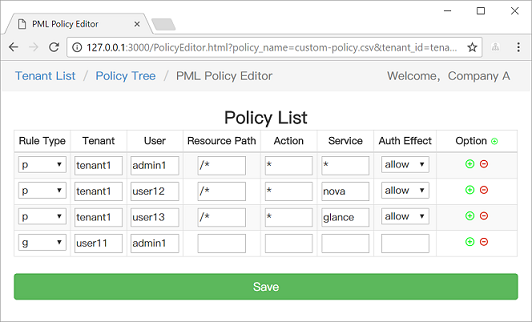
|
||||
|
||||
## Policy persistence
|
||||
|
||||
In Casbin, the policy storage is implemented as an adapter (aka middleware for Casbin). To keep light-weight, we don't put adapter code in the main library (except the default file adapter). A complete list of Casbin adapters is provided as below. Any 3rd-party contribution on a new adapter is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Adapter | Type | Author | Description
|
||||
----|------|----|----
|
||||
[File Adapter (built-in)](https://github.com/casbin/casbin/wiki/Policy-persistence#file-adapter) | File | Casbin | Persistence for [.CSV (Comma-Separated Values)](https://en.wikipedia.org/wiki/Comma-separated_values) files
|
||||
[Filtered File Adapter (built-in)](https://github.com/casbin/casbin#policy-enforcement-at-scale) | File | [@faceless-saint](https://github.com/faceless-saint) | Persistence for [.CSV (Comma-Separated Values)](https://en.wikipedia.org/wiki/Comma-separated_values) files with policy subset loading support
|
||||
[Xorm Adapter](https://github.com/casbin/xorm-adapter) | ORM | Casbin | MySQL, PostgreSQL, TiDB, SQLite, SQL Server, Oracle are supported by [Xorm](https://github.com/go-xorm/xorm/)
|
||||
[Gorm Adapter](https://github.com/casbin/gorm-adapter) | ORM | Casbin | MySQL, PostgreSQL, Sqlite3, SQL Server are supported by [Gorm](https://github.com/jinzhu/gorm/)
|
||||
[Beego ORM Adapter](https://github.com/casbin/beego-orm-adapter) | ORM | Casbin | MySQL, PostgreSQL, Sqlite3 are supported by [Beego ORM](https://beego.me/docs/mvc/model/overview.md)
|
||||
[MongoDB Adapter](https://github.com/casbin/mongodb-adapter) | NoSQL | Casbin | Persistence for [MongoDB](https://www.mongodb.com)
|
||||
[Cassandra Adapter](https://github.com/casbin/cassandra-adapter) | NoSQL | Casbin | Persistence for [Apache Cassandra DB](http://cassandra.apache.org)
|
||||
[Consul Adapter](https://github.com/ankitm123/consul-adapter) | KV store | [@ankitm123](https://github.com/ankitm123) | Persistence for [HashiCorp Consul](https://www.consul.io/)
|
||||
[Redis Adapter](https://github.com/casbin/redis-adapter) | KV store | Casbin | Persistence for [Redis](https://redis.io/)
|
||||
[Protobuf Adapter](https://github.com/casbin/protobuf-adapter) | Stream | Casbin | Persistence for [Google Protocol Buffers](https://developers.google.com/protocol-buffers/)
|
||||
[JSON Adapter](https://github.com/casbin/json-adapter) | String | Casbin | Persistence for [JSON](https://www.json.org/)
|
||||
[String Adapter](https://github.com/qiangmzsx/string-adapter) | String | [@qiangmzsx](https://github.com/qiangmzsx) | Persistence for String
|
||||
[RQLite Adapter](https://github.com/edomosystems/rqlite-adapter) | SQL | [EDOMO Systems](https://github.com/edomosystems) | Persistence for [RQLite](https://github.com/rqlite/rqlite/)
|
||||
[PostgreSQL Adapter](https://github.com/going/casbin-postgres-adapter) | SQL | [Going](https://github.com/going) | Persistence for [PostgreSQL](https://www.postgresql.org/)
|
||||
[RethinkDB Adapter](https://github.com/adityapandey9/rethinkdb-adapter) | NoSQL | [@adityapandey9](https://github.com/adityapandey9) | Persistence for [RethinkDB](https://rethinkdb.com/)
|
||||
[DynamoDB Adapter](https://github.com/HOOQTV/dynacasbin) | NoSQL | [HOOQ](https://github.com/HOOQTV) | Persistence for [Amazon DynamoDB](https://aws.amazon.com/dynamodb/)
|
||||
[Minio/AWS S3 Adapter](https://github.com/Soluto/casbin-minio-adapter) | Object storage | [Soluto](https://github.com/Soluto) | Persistence for [Minio](https://github.com/minio/minio) and [Amazon S3](https://aws.amazon.com/s3/)
|
||||
[Bolt Adapter](https://github.com/wirepair/bolt-adapter) | KV store | [@wirepair](https://github.com/wirepair) | Persistence for [Bolt](https://github.com/boltdb/bolt)
|
||||
|
||||
For details of adapters, please refer to the documentation: https://github.com/casbin/casbin/wiki/Policy-persistence
|
||||
|
||||
## Policy enforcement at scale
|
||||
|
||||
Some adapters support filtered policy management. This means that the policy loaded by Casbin is a subset of the policy in storage based on a given filter. This allows for efficient policy enforcement in large, multi-tenant environments when parsing the entire policy becomes a performance bottleneck.
|
||||
|
||||
To use filtered policies with a supported adapter, simply call the `LoadFilteredPolicy` method. The valid format for the filter parameter depends on the adapter used. To prevent accidental data loss, the `SavePolicy` method is disabled when a filtered policy is loaded.
|
||||
|
||||
For example, the following code snippet uses the built-in filtered file adapter and the RBAC model with domains. In this case, the filter limits the policy to a single domain. Any policy lines for domains other than `"domain1"` are omitted from the loaded policy:
|
||||
|
||||
```go
|
||||
import (
|
||||
"github.com/casbin/casbin"
|
||||
)
|
||||
|
||||
enforcer := casbin.NewEnforcer()
|
||||
|
||||
adapter := fileadapter.NewFilteredAdapter("examples/rbac_with_domains_policy.csv")
|
||||
enforcer.InitWithAdapter("examples/rbac_with_domains_model.conf", adapter)
|
||||
|
||||
filter := &fileadapter.Filter{
|
||||
P: []string{"", "domain1"},
|
||||
G: []string{"", "", "domain1"},
|
||||
}
|
||||
enforcer.LoadFilteredPolicy(filter)
|
||||
|
||||
// The loaded policy now only contains the entries pertaining to "domain1".
|
||||
```
|
||||
|
||||
## Policy consistence between multiple nodes
|
||||
|
||||
We support to use distributed messaging systems like [etcd](https://github.com/coreos/etcd) to keep consistence between multiple Casbin enforcer instances. So our users can concurrently use multiple Casbin enforcers to handle large number of permission checking requests.
|
||||
|
||||
Similar to policy storage adapters, we don't put watcher code in the main library. Any support for a new messaging system should be implemented as a watcher. A complete list of Casbin watchers is provided as below. Any 3rd-party contribution on a new watcher is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Watcher | Type | Author | Description
|
||||
----|------|----|----
|
||||
[Etcd Watcher](https://github.com/casbin/etcd-watcher) | KV store | Casbin | Watcher for [etcd](https://github.com/coreos/etcd)
|
||||
[NATS Watcher](https://github.com/Soluto/casbin-nats-watcher) | Messaging system | [Soluto](https://github.com/Soluto) | Watcher for [NATS](https://nats.io/)
|
||||
[ZooKeeper Watcher](https://github.com/grepsr/casbin-zk-watcher) | KV store | [Grepsr](https://github.com/grepsr) | Watcher for [Apache ZooKeeper](https://zookeeper.apache.org/)
|
||||
[Redis Watcher](https://github.com/billcobbler/casbin-redis-watcher) | KV store | [@billcobbler](https://github.com/billcobbler) | Watcher for [Redis](http://redis.io/)
|
||||
|
||||
## Role manager
|
||||
|
||||
The role manager is used to manage the RBAC role hierarchy (user-role mapping) in Casbin. A role manager can retrieve the role data from Casbin policy rules or external sources such as LDAP, Okta, Auth0, Azure AD, etc. We support different implementations of a role manager. To keep light-weight, we don't put role manager code in the main library (except the default role manager). A complete list of Casbin role managers is provided as below. Any 3rd-party contribution on a new role manager is welcomed, please inform us and I will put it in this list:)
|
||||
|
||||
Role manager | Author | Description
|
||||
----|----|----
|
||||
[Default Role Manager (built-in)](https://github.com/casbin/casbin/blob/master/rbac/default-role-manager/role_manager.go) | Casbin | Supports role hierarchy stored in Casbin policy
|
||||
[Session Role Manager](https://github.com/casbin/session-role-manager) | [EDOMO Systems](https://github.com/edomosystems) | Supports role hierarchy stored in Casbin policy, with time-range-based sessions
|
||||
[Okta Role Manager](https://github.com/casbin/okta-role-manager) | Casbin | Supports role hierarchy stored in [Okta](https://www.okta.com/)
|
||||
[Auth0 Role Manager](https://github.com/casbin/auth0-role-manager) | Casbin | Supports role hierarchy stored in [Auth0](https://auth0.com/)'s [Authorization Extension](https://auth0.com/docs/extensions/authorization-extension/v2)
|
||||
|
||||
For developers: all role managers must implement the [RoleManager](https://github.com/casbin/casbin/blob/master/rbac/role_manager.go) interface. [Session Role Manager](https://github.com/casbin/session-role-manager) can be used as a reference implementation.
|
||||
|
||||
## Multi-threading
|
||||
|
||||
If you use Casbin in a multi-threading manner, you can use the synchronized wrapper of the Casbin enforcer: https://github.com/casbin/casbin/blob/master/enforcer_synced.go.
|
||||
|
||||
It also supports the ``AutoLoad`` feature, which means the Casbin enforcer will automatically load the latest policy rules from DB if it has changed. Call ``StartAutoLoadPolicy()`` to start automatically loading policy periodically and call ``StopAutoLoadPolicy()`` to stop it.
|
||||
|
||||
## Benchmarks
|
||||
|
||||
The overhead of policy enforcement is benchmarked in [model_b_test.go](https://github.com/casbin/casbin/blob/master/model_b_test.go). The testbed is:
|
||||
|
||||
```
|
||||
Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz, 2601 Mhz, 4 Core(s), 8 Logical Processor(s)
|
||||
```
|
||||
|
||||
The benchmarking result of ``go test -bench=. -benchmem`` is as follows (op = an ``Enforce()`` call, ms = millisecond, KB = kilo bytes):
|
||||
|
||||
Test case | Size | Time overhead | Memory overhead
|
||||
----|------|------|----
|
||||
ACL | 2 rules (2 users) | 0.015493 ms/op | 5.649 KB
|
||||
RBAC | 5 rules (2 users, 1 role) | 0.021738 ms/op | 7.522 KB
|
||||
RBAC (small) | 1100 rules (1000 users, 100 roles) | 0.164309 ms/op | 80.620 KB
|
||||
RBAC (medium) | 11000 rules (10000 users, 1000 roles) | 2.258262 ms/op | 765.152 KB
|
||||
RBAC (large) | 110000 rules (100000 users, 10000 roles) | 23.916776 ms/op | 7.606 MB
|
||||
RBAC with resource roles | 6 rules (2 users, 2 roles) | 0.021146 ms/op | 7.906 KB
|
||||
RBAC with domains/tenants | 6 rules (2 users, 1 role, 2 domains) | 0.032696 ms/op | 10.755 KB
|
||||
ABAC | 0 rule (0 user) | 0.007510 ms/op | 2.328 KB
|
||||
RESTful | 5 rules (3 users) | 0.045398 ms/op | 91.774 KB
|
||||
Deny-override | 6 rules (2 users, 1 role) | 0.023281 ms/op | 8.370 KB
|
||||
Priority | 9 rules (2 users, 2 roles) | 0.016389 ms/op | 5.313 KB
|
||||
|
||||
## Examples
|
||||
|
||||
Model | Model file | Policy file
|
||||
----|------|----
|
||||
ACL | [basic_model.conf](https://github.com/casbin/casbin/blob/master/examples/basic_model.conf) | [basic_policy.csv](https://github.com/casbin/casbin/blob/master/examples/basic_policy.csv)
|
||||
ACL with superuser | [basic_model_with_root.conf](https://github.com/casbin/casbin/blob/master/examples/basic_with_root_model.conf) | [basic_policy.csv](https://github.com/casbin/casbin/blob/master/examples/basic_policy.csv)
|
||||
ACL without users | [basic_model_without_users.conf](https://github.com/casbin/casbin/blob/master/examples/basic_without_users_model.conf) | [basic_policy_without_users.csv](https://github.com/casbin/casbin/blob/master/examples/basic_without_users_policy.csv)
|
||||
ACL without resources | [basic_model_without_resources.conf](https://github.com/casbin/casbin/blob/master/examples/basic_without_resources_model.conf) | [basic_policy_without_resources.csv](https://github.com/casbin/casbin/blob/master/examples/basic_without_resources_policy.csv)
|
||||
RBAC | [rbac_model.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_model.conf) | [rbac_policy.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_policy.csv)
|
||||
RBAC with resource roles | [rbac_model_with_resource_roles.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_resource_roles_model.conf) | [rbac_policy_with_resource_roles.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_resource_roles_policy.csv)
|
||||
RBAC with domains/tenants | [rbac_model_with_domains.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_domains_model.conf) | [rbac_policy_with_domains.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_domains_policy.csv)
|
||||
ABAC | [abac_model.conf](https://github.com/casbin/casbin/blob/master/examples/abac_model.conf) | N/A
|
||||
RESTful | [keymatch_model.conf](https://github.com/casbin/casbin/blob/master/examples/keymatch_model.conf) | [keymatch_policy.csv](https://github.com/casbin/casbin/blob/master/examples/keymatch_policy.csv)
|
||||
Deny-override | [rbac_model_with_deny.conf](https://github.com/casbin/casbin/blob/master/examples/rbac_with_deny_model.conf) | [rbac_policy_with_deny.csv](https://github.com/casbin/casbin/blob/master/examples/rbac_with_deny_policy.csv)
|
||||
Priority | [priority_model.conf](https://github.com/casbin/casbin/blob/master/examples/priority_model.conf) | [priority_policy.csv](https://github.com/casbin/casbin/blob/master/examples/priority_policy.csv)
|
||||
|
||||
## How to use Casbin as a service?
|
||||
|
||||
- [Go-Simple-API-Gateway](https://github.com/Soontao/go-simple-api-gateway): A simple API gateway written by golang, supports for authentication and authorization
|
||||
- [Casbin Server](https://github.com/casbin/casbin-server): Casbin as a Service via RESTful, only exposed permission checking API
|
||||
- [middleware-acl](https://github.com/luk4z7/middleware-acl): RESTful access control middleware based on Casbin
|
||||
|
||||
## Our adopters
|
||||
|
||||
### Web frameworks
|
||||
|
||||
- [Beego](https://github.com/astaxie/beego): An open-source, high-performance web framework for Go, via built-in plugin: [plugins/authz](https://github.com/astaxie/beego/blob/master/plugins/authz)
|
||||
- [Caddy](https://github.com/mholt/caddy): Fast, cross-platform HTTP/2 web server with automatic HTTPS, via plugin: [caddy-authz](https://github.com/casbin/caddy-authz)
|
||||
- [Gin](https://github.com/gin-gonic/gin): A HTTP web framework featuring a Martini-like API with much better performance, via plugin: [authz](https://github.com/gin-contrib/authz)
|
||||
- [Revel](https://github.com/revel/revel): A high productivity, full-stack web framework for the Go language, via plugin: [auth/casbin](https://github.com/revel/modules/tree/master/auth/casbin)
|
||||
- [Echo](https://github.com/labstack/echo): High performance, minimalist Go web framework, via plugin: [echo-authz](https://github.com/labstack/echo-contrib/tree/master/casbin) (thanks to [@xqbumu](https://github.com/xqbumu))
|
||||
- [Iris](https://github.com/kataras/iris): The fastest web framework for Go in (THIS) Earth. HTTP/2 Ready-To-GO, via plugin: [casbin](https://github.com/iris-contrib/middleware/tree/master/casbin) (thanks to [@hiveminded](https://github.com/hiveminded))
|
||||
- [Negroni](https://github.com/urfave/negroni): Idiomatic HTTP Middleware for Golang, via plugin: [negroni-authz](https://github.com/casbin/negroni-authz)
|
||||
- [Tango](https://github.com/lunny/tango): Micro & pluggable web framework for Go, via plugin: [authz](https://github.com/tango-contrib/authz)
|
||||
- [Chi](https://github.com/pressly/chi): A lightweight, idiomatic and composable router for building HTTP services, via plugin: [chi-authz](https://github.com/casbin/chi-authz)
|
||||
- [Macaron](https://github.com/go-macaron/macaron): A high productive and modular web framework in Go, via plugin: [authz](https://github.com/go-macaron/authz)
|
||||
- [DotWeb](https://github.com/devfeel/dotweb): Simple and easy go web micro framework, via plugin: [authz](https://github.com/devfeel/middleware/tree/master/authz)
|
||||
- [Baa](https://github.com/go-baa/baa): An express Go web framework with routing, middleware, dependency injection and http context, via plugin: [authz](https://github.com/baa-middleware/authz)
|
||||
|
||||
### Others
|
||||
|
||||
- [Intel RMD](https://github.com/intel/rmd): Intel's resource management daemon, via direct integration, see: [model](https://github.com/intel/rmd/blob/master/etc/rmd/acl/url/model.conf), [policy rules](https://github.com/intel/rmd/blob/master/etc/rmd/acl/url/policy.csv)
|
||||
- [VMware Dispatch](https://github.com/vmware/dispatch): A framework for deploying and managing serverless style applications, via direct integration, see: [model (in code)](https://github.com/vmware/dispatch/blob/master/pkg/identity-manager/handlers.go#L46-L55), [policy rules (in code)](https://github.com/vmware/dispatch/blob/master/pkg/identity-manager/handlers_test.go#L35-L45)
|
||||
- [Banzai Pipeline](https://github.com/banzaicloud/pipeline): [Banzai Cloud](https://github.com/banzaicloud)'s RESTful API to provision or reuse managed Kubernetes clusters in the cloud, via direct integration, see: [model (in code)](https://github.com/banzaicloud/pipeline/blob/master/auth/authz.go#L15-L30), [policy rules (in code)](https://github.com/banzaicloud/pipeline/blob/master/auth/authz.go#L84-L93)
|
||||
- [Docker](https://github.com/docker/docker): The world's leading software container platform, via plugin: [casbin-authz-plugin](https://github.com/casbin/casbin-authz-plugin) ([recommended by Docker](https://docs.docker.com/engine/extend/legacy_plugins/#authorization-plugins))
|
||||
- [Gobis](https://github.com/orange-cloudfoundry/gobis): [Orange](https://github.com/orange-cloudfoundry)'s lightweight API Gateway written in go, via plugin: [casbin](https://github.com/orange-cloudfoundry/gobis-middlewares/tree/master/casbin), see [model (in code)](https://github.com/orange-cloudfoundry/gobis-middlewares/blob/master/casbin/model.go#L52-L65), [policy rules (from request)](https://github.com/orange-cloudfoundry/gobis-middlewares/blob/master/casbin/adapter.go#L46-L64)
|
||||
- [Skydive](https://github.com/skydive-project/skydive): An open source real-time network topology and protocols analyzer, via direct integration, see: [model (in code)](https://github.com/skydive-project/skydive/blob/master/config/config.go#L136-L140), [policy rules](https://github.com/skydive-project/skydive/blob/master/rbac/policy.csv)
|
||||
- [Zenpress](https://github.com/insionng/zenpress): A CMS system written in Golang, via direct integration, see: [model](https://github.com/insionng/zenpress/blob/master/content/config/rbac_model.conf), [policy rules (in Gorm)](https://github.com/insionng/zenpress/blob/master/model/user.go#L53-L77)
|
||||
- [Argo CD](https://github.com/argoproj/argo-cd): GitOps continuous delivery for Kubernetes, via direct integration, see: [model](https://github.com/argoproj/argo-cd/blob/master/util/rbac/model.conf), [policy rules](https://github.com/argoproj/argo-cd/blob/master/util/rbac/builtin-policy.csv)
|
||||
- [EngineerCMS](https://github.com/3xxx/EngineerCMS): A CMS to manage knowledge for engineers, via direct integration, see: [model](https://github.com/3xxx/EngineerCMS/blob/master/conf/rbac_model.conf), [policy rules (in SQLite)](https://github.com/3xxx/EngineerCMS/blob/master/database/engineer.db)
|
||||
- [Cyber Auth API](https://github.com/CyberlifeCN/cyber-auth-api): A Golang authentication API project, via direct integration, see: [model](https://github.com/CyberlifeCN/cyber-auth-api/blob/master/conf/authz_model.conf), [policy rules](https://github.com/CyberlifeCN/cyber-auth-api/blob/master/conf/authz_policy.csv)
|
||||
- [IRIS Community](https://github.com/irisnet/iris-community): Website for IRIS Community Activities, via direct integration, see: [model](https://github.com/irisnet/iris-community/blob/master/authz/authz_model.conf), [policy rules](https://github.com/irisnet/iris-community/blob/master/authz/authz_policy.csv)
|
||||
- [Metadata DB](https://github.com/Bnei-Baruch/mdb): BB archive metadata database, via direct integration, see: [model](https://github.com/Bnei-Baruch/mdb/blob/master/data/permissions_model.conf), [policy rules](https://github.com/Bnei-Baruch/mdb/blob/master/data/permissions_policy.csv)
|
||||
|
||||
## License
|
||||
|
||||
This project is licensed under the [Apache 2.0 license](https://github.com/casbin/casbin/blob/master/LICENSE).
|
||||
|
||||
## Contact
|
||||
|
||||
If you have any issues or feature requests, please contact us. PR is welcomed.
|
||||
- https://github.com/casbin/casbin/issues
|
||||
- hsluoyz@gmail.com
|
||||
- Tencent QQ group: [546057381](//shang.qq.com/wpa/qunwpa?idkey=8ac8b91fc97ace3d383d0035f7aa06f7d670fd8e8d4837347354a31c18fac885)
|
||||
|
||||
## Donation
|
||||
|
||||
[](http://www.patreon.com/yangluo)
|
||||
|
||||

|
||||

|
||||
BIN
vendor/github.com/casbin/casbin/casbin-logo.png
generated
vendored
Normal file
BIN
vendor/github.com/casbin/casbin/casbin-logo.png
generated
vendored
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 34 KiB |
266
vendor/github.com/casbin/casbin/config/config.go
generated
vendored
Normal file
266
vendor/github.com/casbin/casbin/config/config.go
generated
vendored
Normal file
@@ -0,0 +1,266 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package config
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"bytes"
|
||||
"errors"
|
||||
"fmt"
|
||||
"io"
|
||||
"os"
|
||||
"strconv"
|
||||
"strings"
|
||||
"sync"
|
||||
)
|
||||
|
||||
var (
|
||||
// DEFAULT_SECTION specifies the name of a section if no name provided
|
||||
DEFAULT_SECTION = "default"
|
||||
// DEFAULT_COMMENT defines what character(s) indicate a comment `#`
|
||||
DEFAULT_COMMENT = []byte{'#'}
|
||||
// DEFAULT_COMMENT_SEM defines what alternate character(s) indicate a comment `;`
|
||||
DEFAULT_COMMENT_SEM = []byte{';'}
|
||||
// DEFAULT_MULTI_LINE_SEPARATOR defines what character indicates a multi-line content
|
||||
DEFAULT_MULTI_LINE_SEPARATOR = []byte{'\\'}
|
||||
)
|
||||
|
||||
// ConfigInterface defines the behavior of a Config implemenation
|
||||
type ConfigInterface interface {
|
||||
String(key string) string
|
||||
Strings(key string) []string
|
||||
Bool(key string) (bool, error)
|
||||
Int(key string) (int, error)
|
||||
Int64(key string) (int64, error)
|
||||
Float64(key string) (float64, error)
|
||||
Set(key string, value string) error
|
||||
}
|
||||
|
||||
// Config represents an implementation of the ConfigInterface
|
||||
type Config struct {
|
||||
// map is not safe.
|
||||
sync.RWMutex
|
||||
// Section:key=value
|
||||
data map[string]map[string]string
|
||||
}
|
||||
|
||||
// NewConfig create an empty configuration representation from file.
|
||||
func NewConfig(confName string) (ConfigInterface, error) {
|
||||
c := &Config{
|
||||
data: make(map[string]map[string]string),
|
||||
}
|
||||
err := c.parse(confName)
|
||||
return c, err
|
||||
}
|
||||
|
||||
// NewConfigFromText create an empty configuration representation from text.
|
||||
func NewConfigFromText(text string) (ConfigInterface, error) {
|
||||
c := &Config{
|
||||
data: make(map[string]map[string]string),
|
||||
}
|
||||
err := c.parseBuffer(bufio.NewReader(strings.NewReader(text)))
|
||||
return c, err
|
||||
}
|
||||
|
||||
// AddConfig adds a new section->key:value to the configuration.
|
||||
func (c *Config) AddConfig(section string, option string, value string) bool {
|
||||
if section == "" {
|
||||
section = DEFAULT_SECTION
|
||||
}
|
||||
|
||||
if _, ok := c.data[section]; !ok {
|
||||
c.data[section] = make(map[string]string)
|
||||
}
|
||||
|
||||
_, ok := c.data[section][option]
|
||||
c.data[section][option] = value
|
||||
|
||||
return !ok
|
||||
}
|
||||
|
||||
func (c *Config) parse(fname string) (err error) {
|
||||
c.Lock()
|
||||
f, err := os.Open(fname)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer c.Unlock()
|
||||
defer f.Close()
|
||||
|
||||
buf := bufio.NewReader(f)
|
||||
return c.parseBuffer(buf)
|
||||
}
|
||||
|
||||
func (c *Config) parseBuffer(buf *bufio.Reader) error {
|
||||
var section string
|
||||
var lineNum int
|
||||
var buffer bytes.Buffer
|
||||
var canWrite bool
|
||||
for {
|
||||
if canWrite {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
} else {
|
||||
canWrite = false
|
||||
}
|
||||
}
|
||||
lineNum++
|
||||
line, _, err := buf.ReadLine()
|
||||
if err == io.EOF {
|
||||
// force write when buffer is not flushed yet
|
||||
if buffer.Len() > 0 {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
}
|
||||
}
|
||||
break
|
||||
} else if err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
line = bytes.TrimSpace(line)
|
||||
switch {
|
||||
case bytes.Equal(line, []byte{}), bytes.HasPrefix(line, DEFAULT_COMMENT_SEM),
|
||||
bytes.HasPrefix(line, DEFAULT_COMMENT):
|
||||
canWrite = true
|
||||
continue
|
||||
case bytes.HasPrefix(line, []byte{'['}) && bytes.HasSuffix(line, []byte{']'}):
|
||||
// force write when buffer is not flushed yet
|
||||
if buffer.Len() > 0 {
|
||||
if err := c.write(section, lineNum, &buffer); err != nil {
|
||||
return err
|
||||
}
|
||||
canWrite = false
|
||||
}
|
||||
section = string(line[1 : len(line)-1])
|
||||
default:
|
||||
var p []byte
|
||||
if bytes.HasSuffix(line, DEFAULT_MULTI_LINE_SEPARATOR) {
|
||||
p = bytes.TrimSpace(line[:len(line)-1])
|
||||
} else {
|
||||
p = line
|
||||
canWrite = true
|
||||
}
|
||||
|
||||
if _, err := buffer.Write(p); err != nil {
|
||||
return err
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
func (c *Config) write(section string, lineNum int, b *bytes.Buffer) error {
|
||||
if b.Len() <= 0 {
|
||||
return nil
|
||||
}
|
||||
|
||||
optionVal := bytes.SplitN(b.Bytes(), []byte{'='}, 2)
|
||||
if len(optionVal) != 2 {
|
||||
return fmt.Errorf("parse the content error : line %d , %s = ? ", lineNum, optionVal[0])
|
||||
}
|
||||
option := bytes.TrimSpace(optionVal[0])
|
||||
value := bytes.TrimSpace(optionVal[1])
|
||||
c.AddConfig(section, string(option), string(value))
|
||||
|
||||
// flush buffer after adding
|
||||
b.Reset()
|
||||
|
||||
return nil
|
||||
}
|
||||
|
||||
// Bool lookups up the value using the provided key and converts the value to a bool
|
||||
func (c *Config) Bool(key string) (bool, error) {
|
||||
return strconv.ParseBool(c.get(key))
|
||||
}
|
||||
|
||||
// Int lookups up the value using the provided key and converts the value to a int
|
||||
func (c *Config) Int(key string) (int, error) {
|
||||
return strconv.Atoi(c.get(key))
|
||||
}
|
||||
|
||||
// Int64 lookups up the value using the provided key and converts the value to a int64
|
||||
func (c *Config) Int64(key string) (int64, error) {
|
||||
return strconv.ParseInt(c.get(key), 10, 64)
|
||||
}
|
||||
|
||||
// Float64 lookups up the value using the provided key and converts the value to a float64
|
||||
func (c *Config) Float64(key string) (float64, error) {
|
||||
return strconv.ParseFloat(c.get(key), 64)
|
||||
}
|
||||
|
||||
// String lookups up the value using the provided key and converts the value to a string
|
||||
func (c *Config) String(key string) string {
|
||||
return c.get(key)
|
||||
}
|
||||
|
||||
// Strings lookups up the value using the provided key and converts the value to an array of string
|
||||
// by splitting the string by comma
|
||||
func (c *Config) Strings(key string) []string {
|
||||
v := c.get(key)
|
||||
if v == "" {
|
||||
return nil
|
||||
}
|
||||
return strings.Split(v, ",")
|
||||
}
|
||||
|
||||
// Set sets the value for the specific key in the Config
|
||||
func (c *Config) Set(key string, value string) error {
|
||||
c.Lock()
|
||||
defer c.Unlock()
|
||||
if len(key) == 0 {
|
||||
return errors.New("key is empty")
|
||||
}
|
||||
|
||||
var (
|
||||
section string
|
||||
option string
|
||||
)
|
||||
|
||||
keys := strings.Split(strings.ToLower(key), "::")
|
||||
if len(keys) >= 2 {
|
||||
section = keys[0]
|
||||
option = keys[1]
|
||||
} else {
|
||||
option = keys[0]
|
||||
}
|
||||
|
||||
c.AddConfig(section, option, value)
|
||||
return nil
|
||||
}
|
||||
|
||||
// section.key or key
|
||||
func (c *Config) get(key string) string {
|
||||
var (
|
||||
section string
|
||||
option string
|
||||
)
|
||||
|
||||
keys := strings.Split(strings.ToLower(key), "::")
|
||||
if len(keys) >= 2 {
|
||||
section = keys[0]
|
||||
option = keys[1]
|
||||
} else {
|
||||
section = DEFAULT_SECTION
|
||||
option = keys[0]
|
||||
}
|
||||
|
||||
if value, ok := c.data[section][option]; ok {
|
||||
return value
|
||||
}
|
||||
|
||||
return ""
|
||||
}
|
||||
75
vendor/github.com/casbin/casbin/effect/default_effector.go
generated
vendored
Normal file
75
vendor/github.com/casbin/casbin/effect/default_effector.go
generated
vendored
Normal file
@@ -0,0 +1,75 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package effect
|
||||
|
||||
import "github.com/pkg/errors"
|
||||
|
||||
// DefaultEffector is default effector for Casbin.
|
||||
type DefaultEffector struct {
|
||||
}
|
||||
|
||||
// NewDefaultEffector is the constructor for DefaultEffector.
|
||||
func NewDefaultEffector() *DefaultEffector {
|
||||
e := DefaultEffector{}
|
||||
return &e
|
||||
}
|
||||
|
||||
// MergeEffects merges all matching results collected by the enforcer into a single decision.
|
||||
func (e *DefaultEffector) MergeEffects(expr string, effects []Effect, results []float64) (bool, error) {
|
||||
result := false
|
||||
if expr == "some(where (p_eft == allow))" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "!some(where (p_eft == deny))" {
|
||||
result = true
|
||||
for _, eft := range effects {
|
||||
if eft == Deny {
|
||||
result = false
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "some(where (p_eft == allow)) && !some(where (p_eft == deny))" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
} else if eft == Deny {
|
||||
result = false
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if expr == "priority(p_eft) || deny" {
|
||||
result = false
|
||||
for _, eft := range effects {
|
||||
if eft != Indeterminate {
|
||||
if eft == Allow {
|
||||
result = true
|
||||
} else {
|
||||
result = false
|
||||
}
|
||||
break
|
||||
}
|
||||
}
|
||||
} else {
|
||||
return false, errors.New("unsupported effect")
|
||||
}
|
||||
|
||||
return result, nil
|
||||
}
|
||||
31
vendor/github.com/casbin/casbin/effect/effector.go
generated
vendored
Normal file
31
vendor/github.com/casbin/casbin/effect/effector.go
generated
vendored
Normal file
@@ -0,0 +1,31 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package effect
|
||||
|
||||
// Effect is the result for a policy rule.
|
||||
type Effect int
|
||||
|
||||
// Values for policy effect.
|
||||
const (
|
||||
Allow Effect = iota
|
||||
Indeterminate
|
||||
Deny
|
||||
)
|
||||
|
||||
// Effector is the interface for Casbin effectors.
|
||||
type Effector interface {
|
||||
// MergeEffects merges all matching results collected by the enforcer into a single decision.
|
||||
MergeEffects(expr string, effects []Effect, results []float64) (bool, error)
|
||||
}
|
||||
425
vendor/github.com/casbin/casbin/enforcer.go
generated
vendored
Normal file
425
vendor/github.com/casbin/casbin/enforcer.go
generated
vendored
Normal file
@@ -0,0 +1,425 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"fmt"
|
||||
|
||||
"github.com/Knetic/govaluate"
|
||||
|
||||
"github.com/casbin/casbin/effect"
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
"github.com/casbin/casbin/persist/file-adapter"
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/rbac/default-role-manager"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Enforcer is the main interface for authorization enforcement and policy management.
|
||||
type Enforcer struct {
|
||||
modelPath string
|
||||
model model.Model
|
||||
fm model.FunctionMap
|
||||
eft effect.Effector
|
||||
|
||||
adapter persist.Adapter
|
||||
watcher persist.Watcher
|
||||
rm rbac.RoleManager
|
||||
|
||||
enabled bool
|
||||
autoSave bool
|
||||
autoBuildRoleLinks bool
|
||||
}
|
||||
|
||||
// NewEnforcer creates an enforcer via file or DB.
|
||||
// File:
|
||||
// e := casbin.NewEnforcer("path/to/basic_model.conf", "path/to/basic_policy.csv")
|
||||
// MySQL DB:
|
||||
// a := mysqladapter.NewDBAdapter("mysql", "mysql_username:mysql_password@tcp(127.0.0.1:3306)/")
|
||||
// e := casbin.NewEnforcer("path/to/basic_model.conf", a)
|
||||
func NewEnforcer(params ...interface{}) *Enforcer {
|
||||
e := &Enforcer{}
|
||||
e.rm = defaultrolemanager.NewRoleManager(10)
|
||||
e.eft = effect.NewDefaultEffector()
|
||||
|
||||
parsedParamLen := 0
|
||||
if len(params) >= 1 {
|
||||
enableLog, ok := params[len(params)-1].(bool)
|
||||
if ok {
|
||||
e.EnableLog(enableLog)
|
||||
|
||||
parsedParamLen++
|
||||
}
|
||||
}
|
||||
|
||||
if len(params)-parsedParamLen == 2 {
|
||||
switch params[0].(type) {
|
||||
case string:
|
||||
switch params[1].(type) {
|
||||
case string:
|
||||
e.InitWithFile(params[0].(string), params[1].(string))
|
||||
default:
|
||||
e.InitWithAdapter(params[0].(string), params[1].(persist.Adapter))
|
||||
}
|
||||
default:
|
||||
switch params[1].(type) {
|
||||
case string:
|
||||
panic("Invalid parameters for enforcer.")
|
||||
default:
|
||||
e.InitWithModelAndAdapter(params[0].(model.Model), params[1].(persist.Adapter))
|
||||
}
|
||||
}
|
||||
} else if len(params)-parsedParamLen == 1 {
|
||||
switch params[0].(type) {
|
||||
case string:
|
||||
e.InitWithFile(params[0].(string), "")
|
||||
default:
|
||||
e.InitWithModelAndAdapter(params[0].(model.Model), nil)
|
||||
}
|
||||
} else if len(params)-parsedParamLen == 0 {
|
||||
e.InitWithFile("", "")
|
||||
} else {
|
||||
panic("Invalid parameters for enforcer.")
|
||||
}
|
||||
|
||||
return e
|
||||
}
|
||||
|
||||
// InitWithFile initializes an enforcer with a model file and a policy file.
|
||||
func (e *Enforcer) InitWithFile(modelPath string, policyPath string) {
|
||||
a := fileadapter.NewAdapter(policyPath)
|
||||
e.InitWithAdapter(modelPath, a)
|
||||
}
|
||||
|
||||
// InitWithAdapter initializes an enforcer with a database adapter.
|
||||
func (e *Enforcer) InitWithAdapter(modelPath string, adapter persist.Adapter) {
|
||||
m := NewModel(modelPath, "")
|
||||
e.InitWithModelAndAdapter(m, adapter)
|
||||
|
||||
e.modelPath = modelPath
|
||||
}
|
||||
|
||||
// InitWithModelAndAdapter initializes an enforcer with a model and a database adapter.
|
||||
func (e *Enforcer) InitWithModelAndAdapter(m model.Model, adapter persist.Adapter) {
|
||||
e.adapter = adapter
|
||||
e.watcher = nil
|
||||
|
||||
e.model = m
|
||||
e.model.PrintModel()
|
||||
e.fm = model.LoadFunctionMap()
|
||||
|
||||
e.initialize()
|
||||
|
||||
if e.adapter != nil {
|
||||
// error intentionally ignored
|
||||
e.LoadPolicy()
|
||||
}
|
||||
}
|
||||
|
||||
func (e *Enforcer) initialize() {
|
||||
e.enabled = true
|
||||
e.autoSave = true
|
||||
e.autoBuildRoleLinks = true
|
||||
}
|
||||
|
||||
// NewModel creates a model.
|
||||
func NewModel(text ...string) model.Model {
|
||||
m := make(model.Model)
|
||||
|
||||
if len(text) == 2 {
|
||||
if text[0] != "" {
|
||||
m.LoadModel(text[0])
|
||||
}
|
||||
} else if len(text) == 1 {
|
||||
m.LoadModelFromText(text[0])
|
||||
} else if len(text) != 0 {
|
||||
panic("Invalid parameters for model.")
|
||||
}
|
||||
|
||||
return m
|
||||
}
|
||||
|
||||
// LoadModel reloads the model from the model CONF file.
|
||||
// Because the policy is attached to a model, so the policy is invalidated and needs to be reloaded by calling LoadPolicy().
|
||||
func (e *Enforcer) LoadModel() {
|
||||
e.model = NewModel()
|
||||
e.model.LoadModel(e.modelPath)
|
||||
e.model.PrintModel()
|
||||
e.fm = model.LoadFunctionMap()
|
||||
}
|
||||
|
||||
// GetModel gets the current model.
|
||||
func (e *Enforcer) GetModel() model.Model {
|
||||
return e.model
|
||||
}
|
||||
|
||||
// SetModel sets the current model.
|
||||
func (e *Enforcer) SetModel(m model.Model) {
|
||||
e.model = m
|
||||
e.fm = model.LoadFunctionMap()
|
||||
}
|
||||
|
||||
// GetAdapter gets the current adapter.
|
||||
func (e *Enforcer) GetAdapter() persist.Adapter {
|
||||
return e.adapter
|
||||
}
|
||||
|
||||
// SetAdapter sets the current adapter.
|
||||
func (e *Enforcer) SetAdapter(adapter persist.Adapter) {
|
||||
e.adapter = adapter
|
||||
}
|
||||
|
||||
// SetWatcher sets the current watcher.
|
||||
func (e *Enforcer) SetWatcher(watcher persist.Watcher) {
|
||||
e.watcher = watcher
|
||||
// error intentionally ignored
|
||||
watcher.SetUpdateCallback(func(string) { e.LoadPolicy() })
|
||||
}
|
||||
|
||||
// SetRoleManager sets the current role manager.
|
||||
func (e *Enforcer) SetRoleManager(rm rbac.RoleManager) {
|
||||
e.rm = rm
|
||||
}
|
||||
|
||||
// SetEffector sets the current effector.
|
||||
func (e *Enforcer) SetEffector(eft effect.Effector) {
|
||||
e.eft = eft
|
||||
}
|
||||
|
||||
// ClearPolicy clears all policy.
|
||||
func (e *Enforcer) ClearPolicy() {
|
||||
e.model.ClearPolicy()
|
||||
}
|
||||
|
||||
// LoadPolicy reloads the policy from file/database.
|
||||
func (e *Enforcer) LoadPolicy() error {
|
||||
e.model.ClearPolicy()
|
||||
if err := e.adapter.LoadPolicy(e.model); err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
e.model.PrintPolicy()
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// LoadFilteredPolicy reloads a filtered policy from file/database.
|
||||
func (e *Enforcer) LoadFilteredPolicy(filter interface{}) error {
|
||||
e.model.ClearPolicy()
|
||||
|
||||
var filteredAdapter persist.FilteredAdapter
|
||||
|
||||
// Attempt to cast the Adapter as a FilteredAdapter
|
||||
switch e.adapter.(type) {
|
||||
case persist.FilteredAdapter:
|
||||
filteredAdapter = e.adapter.(persist.FilteredAdapter)
|
||||
default:
|
||||
return errors.New("filtered policies are not supported by this adapter")
|
||||
}
|
||||
if err := filteredAdapter.LoadFilteredPolicy(e.model, filter); err != nil {
|
||||
return err
|
||||
}
|
||||
|
||||
e.model.PrintPolicy()
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
func (e *Enforcer) IsFiltered() bool {
|
||||
filteredAdapter, ok := e.adapter.(persist.FilteredAdapter)
|
||||
if !ok {
|
||||
return false
|
||||
}
|
||||
return filteredAdapter.IsFiltered()
|
||||
}
|
||||
|
||||
// SavePolicy saves the current policy (usually after changed with Casbin API) back to file/database.
|
||||
func (e *Enforcer) SavePolicy() error {
|
||||
if e.IsFiltered() {
|
||||
return errors.New("cannot save a filtered policy")
|
||||
}
|
||||
if err := e.adapter.SavePolicy(e.model); err != nil {
|
||||
return err
|
||||
}
|
||||
if e.watcher != nil {
|
||||
return e.watcher.Update()
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
// EnableEnforce changes the enforcing state of Casbin, when Casbin is disabled, all access will be allowed by the Enforce() function.
|
||||
func (e *Enforcer) EnableEnforce(enable bool) {
|
||||
e.enabled = enable
|
||||
}
|
||||
|
||||
// EnableLog changes whether to print Casbin log to the standard output.
|
||||
func (e *Enforcer) EnableLog(enable bool) {
|
||||
util.EnableLog = enable
|
||||
}
|
||||
|
||||
// EnableAutoSave controls whether to save a policy rule automatically to the adapter when it is added or removed.
|
||||
func (e *Enforcer) EnableAutoSave(autoSave bool) {
|
||||
e.autoSave = autoSave
|
||||
}
|
||||
|
||||
// EnableAutoBuildRoleLinks controls whether to rebuild the role inheritance relations when a role is added or deleted.
|
||||
func (e *Enforcer) EnableAutoBuildRoleLinks(autoBuildRoleLinks bool) {
|
||||
e.autoBuildRoleLinks = autoBuildRoleLinks
|
||||
}
|
||||
|
||||
// BuildRoleLinks manually rebuild the role inheritance relations.
|
||||
func (e *Enforcer) BuildRoleLinks() {
|
||||
// error intentionally ignored
|
||||
e.rm.Clear()
|
||||
e.model.BuildRoleLinks(e.rm)
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
func (e *Enforcer) Enforce(rvals ...interface{}) bool {
|
||||
if !e.enabled {
|
||||
return true
|
||||
}
|
||||
|
||||
functions := make(map[string]govaluate.ExpressionFunction)
|
||||
for key, function := range e.fm {
|
||||
functions[key] = function
|
||||
}
|
||||
if _, ok := e.model["g"]; ok {
|
||||
for key, ast := range e.model["g"] {
|
||||
rm := ast.RM
|
||||
functions[key] = util.GenerateGFunction(rm)
|
||||
}
|
||||
}
|
||||
|
||||
expString := e.model["m"]["m"].Value
|
||||
expression, _ := govaluate.NewEvaluableExpressionWithFunctions(expString, functions)
|
||||
|
||||
var policyEffects []effect.Effect
|
||||
var matcherResults []float64
|
||||
if policyLen := len(e.model["p"]["p"].Policy); policyLen != 0 {
|
||||
policyEffects = make([]effect.Effect, policyLen)
|
||||
matcherResults = make([]float64, policyLen)
|
||||
|
||||
for i, pvals := range e.model["p"]["p"].Policy {
|
||||
// util.LogPrint("Policy Rule: ", pvals)
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
for j, token := range e.model["r"]["r"].Tokens {
|
||||
parameters[token] = rvals[j]
|
||||
}
|
||||
for j, token := range e.model["p"]["p"].Tokens {
|
||||
parameters[token] = pvals[j]
|
||||
}
|
||||
|
||||
result, err := expression.Evaluate(parameters)
|
||||
// util.LogPrint("Result: ", result)
|
||||
|
||||
if err != nil {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
panic(err)
|
||||
}
|
||||
|
||||
switch result.(type) {
|
||||
case bool:
|
||||
if !result.(bool) {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
continue
|
||||
}
|
||||
case float64:
|
||||
if result.(float64) == 0 {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
continue
|
||||
} else {
|
||||
matcherResults[i] = result.(float64)
|
||||
}
|
||||
default:
|
||||
panic(errors.New("matcher result should be bool, int or float"))
|
||||
}
|
||||
|
||||
if eft, ok := parameters["p_eft"]; ok {
|
||||
if eft == "allow" {
|
||||
policyEffects[i] = effect.Allow
|
||||
} else if eft == "deny" {
|
||||
policyEffects[i] = effect.Deny
|
||||
} else {
|
||||
policyEffects[i] = effect.Indeterminate
|
||||
}
|
||||
} else {
|
||||
policyEffects[i] = effect.Allow
|
||||
}
|
||||
|
||||
if e.model["e"]["e"].Value == "priority(p_eft) || deny" {
|
||||
break
|
||||
}
|
||||
|
||||
}
|
||||
} else {
|
||||
policyEffects = make([]effect.Effect, 1)
|
||||
matcherResults = make([]float64, 1)
|
||||
|
||||
parameters := make(map[string]interface{}, 8)
|
||||
for j, token := range e.model["r"]["r"].Tokens {
|
||||
parameters[token] = rvals[j]
|
||||
}
|
||||
for _, token := range e.model["p"]["p"].Tokens {
|
||||
parameters[token] = ""
|
||||
}
|
||||
|
||||
result, err := expression.Evaluate(parameters)
|
||||
// util.LogPrint("Result: ", result)
|
||||
|
||||
if err != nil {
|
||||
policyEffects[0] = effect.Indeterminate
|
||||
panic(err)
|
||||
}
|
||||
|
||||
if result.(bool) {
|
||||
policyEffects[0] = effect.Allow
|
||||
} else {
|
||||
policyEffects[0] = effect.Indeterminate
|
||||
}
|
||||
}
|
||||
|
||||
// util.LogPrint("Rule Results: ", policyEffects)
|
||||
|
||||
result, err := e.eft.MergeEffects(e.model["e"]["e"].Value, policyEffects, matcherResults)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
// only generate the request --> result string if the message
|
||||
// is going to be logged.
|
||||
if util.EnableLog {
|
||||
reqStr := "Request: "
|
||||
for i, rval := range rvals {
|
||||
if i != len(rvals)-1 {
|
||||
reqStr += fmt.Sprintf("%v, ", rval)
|
||||
} else {
|
||||
reqStr += fmt.Sprintf("%v", rval)
|
||||
}
|
||||
}
|
||||
reqStr += fmt.Sprintf(" ---> %t", result)
|
||||
util.LogPrint(reqStr)
|
||||
}
|
||||
|
||||
return result
|
||||
}
|
||||
74
vendor/github.com/casbin/casbin/enforcer_cached.go
generated
vendored
Normal file
74
vendor/github.com/casbin/casbin/enforcer_cached.go
generated
vendored
Normal file
@@ -0,0 +1,74 @@
|
||||
// Copyright 2018 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"sync"
|
||||
)
|
||||
|
||||
// CachedEnforcer wraps Enforcer and provides decision cache
|
||||
type CachedEnforcer struct {
|
||||
*Enforcer
|
||||
m map[string]bool
|
||||
enableCache bool
|
||||
locker *sync.Mutex
|
||||
}
|
||||
|
||||
// NewCachedEnforcer creates a cached enforcer via file or DB.
|
||||
func NewCachedEnforcer(params ...interface{}) *CachedEnforcer {
|
||||
e := &CachedEnforcer{}
|
||||
e.Enforcer = NewEnforcer(params...)
|
||||
e.enableCache = true
|
||||
e.m = make(map[string]bool)
|
||||
e.locker = new(sync.Mutex)
|
||||
return e
|
||||
}
|
||||
|
||||
// EnableCache determines whether to enable cache on Enforce(). When enableCache is enabled, cached result (true | false) will be returned for previous decisions.
|
||||
func (e *CachedEnforcer) EnableCache(enableCache bool) {
|
||||
e.enableCache = enableCache
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
// if rvals is not string , ingore the cache
|
||||
func (e *CachedEnforcer) Enforce(rvals ...interface{}) bool {
|
||||
if !e.enableCache {
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
|
||||
key := ""
|
||||
for _, rval := range rvals {
|
||||
if val, ok := rval.(string); ok {
|
||||
key += val + "$$"
|
||||
} else {
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
}
|
||||
|
||||
e.locker.Lock()
|
||||
defer e.locker.Unlock()
|
||||
if _, ok := e.m[key]; ok {
|
||||
return e.m[key]
|
||||
} else {
|
||||
res := e.Enforcer.Enforce(rvals...)
|
||||
e.m[key] = res
|
||||
return res
|
||||
}
|
||||
}
|
||||
|
||||
// InvalidateCache deletes all the existing cached decisions.
|
||||
func (e *CachedEnforcer) InvalidateCache() {
|
||||
e.m = make(map[string]bool)
|
||||
}
|
||||
102
vendor/github.com/casbin/casbin/enforcer_safe.go
generated
vendored
Normal file
102
vendor/github.com/casbin/casbin/enforcer_safe.go
generated
vendored
Normal file
@@ -0,0 +1,102 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"fmt"
|
||||
)
|
||||
|
||||
// NewEnforcerSafe calls NewEnforcer in a safe way, returns error instead of causing panic.
|
||||
func NewEnforcerSafe(params ...interface{}) (e *Enforcer, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
e = nil
|
||||
}
|
||||
}()
|
||||
|
||||
e = NewEnforcer(params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// LoadModelSafe calls LoadModel in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) LoadModelSafe() (err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
}
|
||||
}()
|
||||
|
||||
e.LoadModel()
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// EnforceSafe calls Enforce in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) EnforceSafe(rvals ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.Enforce(rvals...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// AddPolicySafe calls AddPolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) AddPolicySafe(params ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.AddNamedPolicy("p", params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// RemovePolicySafe calls RemovePolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) RemovePolicySafe(params ...interface{}) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.RemoveNamedPolicy("p", params...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicySafe calls RemoveFilteredPolicy in a safe way, returns error instead of causing panic.
|
||||
func (e *Enforcer) RemoveFilteredPolicySafe(fieldIndex int, fieldValues ...string) (result bool, err error) {
|
||||
defer func() {
|
||||
if r := recover(); r != nil {
|
||||
err = fmt.Errorf("%v", r)
|
||||
result = false
|
||||
}
|
||||
}()
|
||||
|
||||
result = e.RemoveFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
err = nil
|
||||
return
|
||||
}
|
||||
223
vendor/github.com/casbin/casbin/enforcer_synced.go
generated
vendored
Normal file
223
vendor/github.com/casbin/casbin/enforcer_synced.go
generated
vendored
Normal file
@@ -0,0 +1,223 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
import (
|
||||
"log"
|
||||
"sync"
|
||||
"time"
|
||||
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// SyncedEnforcer wraps Enforcer and provides synchronized access
|
||||
type SyncedEnforcer struct {
|
||||
*Enforcer
|
||||
m sync.RWMutex
|
||||
autoLoad bool
|
||||
}
|
||||
|
||||
// NewSyncedEnforcer creates a synchronized enforcer via file or DB.
|
||||
func NewSyncedEnforcer(params ...interface{}) *SyncedEnforcer {
|
||||
e := &SyncedEnforcer{}
|
||||
e.Enforcer = NewEnforcer(params...)
|
||||
e.autoLoad = false
|
||||
return e
|
||||
}
|
||||
|
||||
// StartAutoLoadPolicy starts a go routine that will every specified duration call LoadPolicy
|
||||
func (e *SyncedEnforcer) StartAutoLoadPolicy(d time.Duration) {
|
||||
e.autoLoad = true
|
||||
go func() {
|
||||
n := 1
|
||||
log.Print("Start automatically load policy")
|
||||
for {
|
||||
if !e.autoLoad {
|
||||
log.Print("Stop automatically load policy")
|
||||
break
|
||||
}
|
||||
|
||||
// error intentionally ignored
|
||||
e.LoadPolicy()
|
||||
// Uncomment this line to see when the policy is loaded.
|
||||
// log.Print("Load policy for time: ", n)
|
||||
n++
|
||||
time.Sleep(d)
|
||||
}
|
||||
}()
|
||||
}
|
||||
|
||||
// StopAutoLoadPolicy causes the go routine to exit.
|
||||
func (e *SyncedEnforcer) StopAutoLoadPolicy() {
|
||||
e.autoLoad = false
|
||||
}
|
||||
|
||||
// SetWatcher sets the current watcher.
|
||||
func (e *SyncedEnforcer) SetWatcher(watcher persist.Watcher) {
|
||||
e.watcher = watcher
|
||||
// error intentionally ignored
|
||||
watcher.SetUpdateCallback(func(string) { e.LoadPolicy() })
|
||||
}
|
||||
|
||||
// ClearPolicy clears all policy.
|
||||
func (e *SyncedEnforcer) ClearPolicy() {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
e.Enforcer.ClearPolicy()
|
||||
}
|
||||
|
||||
// LoadPolicy reloads the policy from file/database.
|
||||
func (e *SyncedEnforcer) LoadPolicy() error {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.LoadPolicy()
|
||||
}
|
||||
|
||||
// SavePolicy saves the current policy (usually after changed with Casbin API) back to file/database.
|
||||
func (e *SyncedEnforcer) SavePolicy() error {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.SavePolicy()
|
||||
}
|
||||
|
||||
// BuildRoleLinks manually rebuild the role inheritance relations.
|
||||
func (e *SyncedEnforcer) BuildRoleLinks() {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
e.Enforcer.BuildRoleLinks()
|
||||
}
|
||||
|
||||
// Enforce decides whether a "subject" can access a "object" with the operation "action", input parameters are usually: (sub, obj, act).
|
||||
func (e *SyncedEnforcer) Enforce(rvals ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.Enforce(rvals...)
|
||||
}
|
||||
|
||||
// GetAllSubjects gets the list of subjects that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllSubjects() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllSubjects()
|
||||
}
|
||||
|
||||
// GetAllObjects gets the list of objects that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllObjects() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllObjects()
|
||||
}
|
||||
|
||||
// GetAllActions gets the list of actions that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllActions() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllActions()
|
||||
}
|
||||
|
||||
// GetAllRoles gets the list of roles that show up in the current policy.
|
||||
func (e *SyncedEnforcer) GetAllRoles() []string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetAllRoles()
|
||||
}
|
||||
|
||||
// GetPolicy gets all the authorization rules in the policy.
|
||||
func (e *SyncedEnforcer) GetPolicy() [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetPolicy()
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets all the authorization rules in the policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) GetFilteredPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetFilteredPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *SyncedEnforcer) GetGroupingPolicy() [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetGroupingPolicy()
|
||||
}
|
||||
|
||||
// GetFilteredGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) GetFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.GetFilteredGroupingPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasPolicy determines whether an authorization rule exists.
|
||||
func (e *SyncedEnforcer) HasPolicy(params ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.HasPolicy(params...)
|
||||
}
|
||||
|
||||
// AddPolicy adds an authorization rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *SyncedEnforcer) AddPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddPolicy(params...)
|
||||
}
|
||||
|
||||
// RemovePolicy removes an authorization rule from the current policy.
|
||||
func (e *SyncedEnforcer) RemovePolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemovePolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes an authorization rule from the current policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) RemoveFilteredPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveFilteredPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasGroupingPolicy determines whether a role inheritance rule exists.
|
||||
func (e *SyncedEnforcer) HasGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.RLock()
|
||||
defer e.m.RUnlock()
|
||||
return e.Enforcer.HasGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// AddGroupingPolicy adds a role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *SyncedEnforcer) AddGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveGroupingPolicy removes a role inheritance rule from the current policy.
|
||||
func (e *SyncedEnforcer) RemoveGroupingPolicy(params ...interface{}) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveGroupingPolicy(params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredGroupingPolicy removes a role inheritance rule from the current policy, field filters can be specified.
|
||||
func (e *SyncedEnforcer) RemoveFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.RemoveFilteredGroupingPolicy(fieldIndex, fieldValues...)
|
||||
}
|
||||
85
vendor/github.com/casbin/casbin/internal_api.go
generated
vendored
Normal file
85
vendor/github.com/casbin/casbin/internal_api.go
generated
vendored
Normal file
@@ -0,0 +1,85 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
const (
|
||||
notImplemented = "not implemented"
|
||||
)
|
||||
|
||||
// addPolicy adds a rule to the current policy.
|
||||
func (e *Enforcer) addPolicy(sec string, ptype string, rule []string) bool {
|
||||
ruleAdded := e.model.AddPolicy(sec, ptype, rule)
|
||||
if !ruleAdded {
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.AddPolicy(sec, ptype, rule); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// removePolicy removes a rule from the current policy.
|
||||
func (e *Enforcer) removePolicy(sec string, ptype string, rule []string) bool {
|
||||
ruleRemoved := e.model.RemovePolicy(sec, ptype, rule)
|
||||
if !ruleRemoved {
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.RemovePolicy(sec, ptype, rule); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// removeFilteredPolicy removes rules based on field filters from the current policy.
|
||||
func (e *Enforcer) removeFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
ruleRemoved := e.model.RemoveFilteredPolicy(sec, ptype, fieldIndex, fieldValues...)
|
||||
if !ruleRemoved {
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
if e.adapter != nil && e.autoSave {
|
||||
if err := e.adapter.RemoveFilteredPolicy(sec, ptype, fieldIndex, fieldValues...); err != nil {
|
||||
if err.Error() != notImplemented {
|
||||
panic(err)
|
||||
}
|
||||
}
|
||||
if e.watcher != nil {
|
||||
// error intentionally ignored
|
||||
e.watcher.Update()
|
||||
}
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
265
vendor/github.com/casbin/casbin/management_api.go
generated
vendored
Normal file
265
vendor/github.com/casbin/casbin/management_api.go
generated
vendored
Normal file
@@ -0,0 +1,265 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetAllSubjects gets the list of subjects that show up in the current policy.
|
||||
func (e *Enforcer) GetAllSubjects() []string {
|
||||
return e.GetAllNamedSubjects("p")
|
||||
}
|
||||
|
||||
// GetAllNamedSubjects gets the list of subjects that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedSubjects(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 0)
|
||||
}
|
||||
|
||||
// GetAllObjects gets the list of objects that show up in the current policy.
|
||||
func (e *Enforcer) GetAllObjects() []string {
|
||||
return e.GetAllNamedObjects("p")
|
||||
}
|
||||
|
||||
// GetAllNamedObjects gets the list of objects that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedObjects(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 1)
|
||||
}
|
||||
|
||||
// GetAllActions gets the list of actions that show up in the current policy.
|
||||
func (e *Enforcer) GetAllActions() []string {
|
||||
return e.GetAllNamedActions("p")
|
||||
}
|
||||
|
||||
// GetAllNamedActions gets the list of actions that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedActions(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("p", ptype, 2)
|
||||
}
|
||||
|
||||
// GetAllRoles gets the list of roles that show up in the current policy.
|
||||
func (e *Enforcer) GetAllRoles() []string {
|
||||
return e.GetAllNamedRoles("g")
|
||||
}
|
||||
|
||||
// GetAllNamedRoles gets the list of roles that show up in the current named policy.
|
||||
func (e *Enforcer) GetAllNamedRoles(ptype string) []string {
|
||||
return e.model.GetValuesForFieldInPolicy("g", ptype, 1)
|
||||
}
|
||||
|
||||
// GetPolicy gets all the authorization rules in the policy.
|
||||
func (e *Enforcer) GetPolicy() [][]string {
|
||||
return e.GetNamedPolicy("p")
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets all the authorization rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.GetFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetNamedPolicy gets all the authorization rules in the named policy.
|
||||
func (e *Enforcer) GetNamedPolicy(ptype string) [][]string {
|
||||
return e.model.GetPolicy("p", ptype)
|
||||
}
|
||||
|
||||
// GetFilteredNamedPolicy gets all the authorization rules in the named policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredNamedPolicy(ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.model.GetFilteredPolicy("p", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *Enforcer) GetGroupingPolicy() [][]string {
|
||||
return e.GetNamedGroupingPolicy("g")
|
||||
}
|
||||
|
||||
// GetFilteredGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.GetFilteredNamedGroupingPolicy("g", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// GetNamedGroupingPolicy gets all the role inheritance rules in the policy.
|
||||
func (e *Enforcer) GetNamedGroupingPolicy(ptype string) [][]string {
|
||||
return e.model.GetPolicy("g", ptype)
|
||||
}
|
||||
|
||||
// GetFilteredNamedGroupingPolicy gets all the role inheritance rules in the policy, field filters can be specified.
|
||||
func (e *Enforcer) GetFilteredNamedGroupingPolicy(ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
return e.model.GetFilteredPolicy("g", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasPolicy determines whether an authorization rule exists.
|
||||
func (e *Enforcer) HasPolicy(params ...interface{}) bool {
|
||||
return e.HasNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// HasNamedPolicy determines whether a named authorization rule exists.
|
||||
func (e *Enforcer) HasNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
return e.model.HasPolicy("p", ptype, strSlice)
|
||||
}
|
||||
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
return e.model.HasPolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
// AddPolicy adds an authorization rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddPolicy(params ...interface{}) bool {
|
||||
return e.AddNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// AddNamedPolicy adds an authorization rule to the current named policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleAdded bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleAdded = e.addPolicy("p", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleAdded = e.addPolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// RemovePolicy removes an authorization rule from the current policy.
|
||||
func (e *Enforcer) RemovePolicy(params ...interface{}) bool {
|
||||
return e.RemoveNamedPolicy("p", params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes an authorization rule from the current policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
return e.RemoveFilteredNamedPolicy("p", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// RemoveNamedPolicy removes an authorization rule from the current named policy.
|
||||
func (e *Enforcer) RemoveNamedPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleRemoved bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleRemoved = e.removePolicy("p", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleRemoved = e.removePolicy("p", ptype, policy)
|
||||
}
|
||||
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// RemoveFilteredNamedPolicy removes an authorization rule from the current named policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredNamedPolicy(ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
return e.removeFilteredPolicy("p", ptype, fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// HasGroupingPolicy determines whether a role inheritance rule exists.
|
||||
func (e *Enforcer) HasGroupingPolicy(params ...interface{}) bool {
|
||||
return e.HasNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// HasNamedGroupingPolicy determines whether a named role inheritance rule exists.
|
||||
func (e *Enforcer) HasNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
return e.model.HasPolicy("g", ptype, strSlice)
|
||||
}
|
||||
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
return e.model.HasPolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
// AddGroupingPolicy adds a role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddGroupingPolicy(params ...interface{}) bool {
|
||||
return e.AddNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// AddNamedGroupingPolicy adds a named role inheritance rule to the current policy.
|
||||
// If the rule already exists, the function returns false and the rule will not be added.
|
||||
// Otherwise the function returns true by adding the new rule.
|
||||
func (e *Enforcer) AddNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleAdded bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleAdded = e.addPolicy("g", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleAdded = e.addPolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleAdded
|
||||
}
|
||||
|
||||
// RemoveGroupingPolicy removes a role inheritance rule from the current policy.
|
||||
func (e *Enforcer) RemoveGroupingPolicy(params ...interface{}) bool {
|
||||
return e.RemoveNamedGroupingPolicy("g", params...)
|
||||
}
|
||||
|
||||
// RemoveFilteredGroupingPolicy removes a role inheritance rule from the current policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredGroupingPolicy(fieldIndex int, fieldValues ...string) bool {
|
||||
return e.RemoveFilteredNamedGroupingPolicy("g", fieldIndex, fieldValues...)
|
||||
}
|
||||
|
||||
// RemoveNamedGroupingPolicy removes a role inheritance rule from the current named policy.
|
||||
func (e *Enforcer) RemoveNamedGroupingPolicy(ptype string, params ...interface{}) bool {
|
||||
var ruleRemoved bool
|
||||
if strSlice, ok := params[0].([]string); len(params) == 1 && ok {
|
||||
ruleRemoved = e.removePolicy("g", ptype, strSlice)
|
||||
} else {
|
||||
policy := make([]string, 0)
|
||||
for _, param := range params {
|
||||
policy = append(policy, param.(string))
|
||||
}
|
||||
|
||||
ruleRemoved = e.removePolicy("g", ptype, policy)
|
||||
}
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// RemoveFilteredNamedGroupingPolicy removes a role inheritance rule from the current named policy, field filters can be specified.
|
||||
func (e *Enforcer) RemoveFilteredNamedGroupingPolicy(ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
ruleRemoved := e.removeFilteredPolicy("g", ptype, fieldIndex, fieldValues...)
|
||||
|
||||
if e.autoBuildRoleLinks {
|
||||
e.BuildRoleLinks()
|
||||
}
|
||||
return ruleRemoved
|
||||
}
|
||||
|
||||
// AddFunction adds a customized function.
|
||||
func (e *Enforcer) AddFunction(name string, function func(args ...interface{}) (interface{}, error)) {
|
||||
e.fm.AddFunction(name, function)
|
||||
}
|
||||
60
vendor/github.com/casbin/casbin/model/assertion.go
generated
vendored
Normal file
60
vendor/github.com/casbin/casbin/model/assertion.go
generated
vendored
Normal file
@@ -0,0 +1,60 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Assertion represents an expression in a section of the model.
|
||||
// For example: r = sub, obj, act
|
||||
type Assertion struct {
|
||||
Key string
|
||||
Value string
|
||||
Tokens []string
|
||||
Policy [][]string
|
||||
RM rbac.RoleManager
|
||||
}
|
||||
|
||||
func (ast *Assertion) buildRoleLinks(rm rbac.RoleManager) {
|
||||
ast.RM = rm
|
||||
count := strings.Count(ast.Value, "_")
|
||||
for _, rule := range ast.Policy {
|
||||
if count < 2 {
|
||||
panic(errors.New("the number of \"_\" in role definition should be at least 2"))
|
||||
}
|
||||
if len(rule) < count {
|
||||
panic(errors.New("grouping policy elements do not meet role definition"))
|
||||
}
|
||||
|
||||
if count == 2 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1])
|
||||
} else if count == 3 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1], rule[2])
|
||||
} else if count == 4 {
|
||||
// error intentionally ignored
|
||||
ast.RM.AddLink(rule[0], rule[1], rule[2], rule[3])
|
||||
}
|
||||
}
|
||||
|
||||
util.LogPrint("Role links for: " + ast.Key)
|
||||
ast.RM.PrintRoles()
|
||||
}
|
||||
40
vendor/github.com/casbin/casbin/model/function.go
generated
vendored
Normal file
40
vendor/github.com/casbin/casbin/model/function.go
generated
vendored
Normal file
@@ -0,0 +1,40 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import "github.com/casbin/casbin/util"
|
||||
|
||||
// FunctionMap represents the collection of Function.
|
||||
type FunctionMap map[string]func(args ...interface{}) (interface{}, error)
|
||||
|
||||
// Function represents a function that is used in the matchers, used to get attributes in ABAC.
|
||||
type Function func(args ...interface{}) (interface{}, error)
|
||||
|
||||
// AddFunction adds an expression function.
|
||||
func (fm FunctionMap) AddFunction(name string, function Function) {
|
||||
fm[name] = function
|
||||
}
|
||||
|
||||
// LoadFunctionMap loads an initial function map.
|
||||
func LoadFunctionMap() FunctionMap {
|
||||
fm := make(FunctionMap)
|
||||
|
||||
fm.AddFunction("keyMatch", util.KeyMatchFunc)
|
||||
fm.AddFunction("keyMatch2", util.KeyMatch2Func)
|
||||
fm.AddFunction("regexMatch", util.RegexMatchFunc)
|
||||
fm.AddFunction("ipMatch", util.IPMatchFunc)
|
||||
|
||||
return fm
|
||||
}
|
||||
129
vendor/github.com/casbin/casbin/model/model.go
generated
vendored
Normal file
129
vendor/github.com/casbin/casbin/model/model.go
generated
vendored
Normal file
@@ -0,0 +1,129 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"strconv"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/config"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Model represents the whole access control model.
|
||||
type Model map[string]AssertionMap
|
||||
|
||||
// AssertionMap is the collection of assertions, can be "r", "p", "g", "e", "m".
|
||||
type AssertionMap map[string]*Assertion
|
||||
|
||||
var sectionNameMap = map[string]string{
|
||||
"r": "request_definition",
|
||||
"p": "policy_definition",
|
||||
"g": "role_definition",
|
||||
"e": "policy_effect",
|
||||
"m": "matchers",
|
||||
}
|
||||
|
||||
func loadAssertion(model Model, cfg config.ConfigInterface, sec string, key string) bool {
|
||||
value := cfg.String(sectionNameMap[sec] + "::" + key)
|
||||
return model.AddDef(sec, key, value)
|
||||
}
|
||||
|
||||
// AddDef adds an assertion to the model.
|
||||
func (model Model) AddDef(sec string, key string, value string) bool {
|
||||
ast := Assertion{}
|
||||
ast.Key = key
|
||||
ast.Value = value
|
||||
|
||||
if ast.Value == "" {
|
||||
return false
|
||||
}
|
||||
|
||||
if sec == "r" || sec == "p" {
|
||||
ast.Tokens = strings.Split(ast.Value, ", ")
|
||||
for i := range ast.Tokens {
|
||||
ast.Tokens[i] = key + "_" + ast.Tokens[i]
|
||||
}
|
||||
} else {
|
||||
ast.Value = util.RemoveComments(util.EscapeAssertion(ast.Value))
|
||||
}
|
||||
|
||||
_, ok := model[sec]
|
||||
if !ok {
|
||||
model[sec] = make(AssertionMap)
|
||||
}
|
||||
|
||||
model[sec][key] = &ast
|
||||
return true
|
||||
}
|
||||
|
||||
func getKeySuffix(i int) string {
|
||||
if i == 1 {
|
||||
return ""
|
||||
}
|
||||
|
||||
return strconv.Itoa(i)
|
||||
}
|
||||
|
||||
func loadSection(model Model, cfg config.ConfigInterface, sec string) {
|
||||
i := 1
|
||||
for {
|
||||
if !loadAssertion(model, cfg, sec, sec+getKeySuffix(i)) {
|
||||
break
|
||||
} else {
|
||||
i++
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// LoadModel loads the model from model CONF file.
|
||||
func (model Model) LoadModel(path string) {
|
||||
cfg, err := config.NewConfig(path)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
loadSection(model, cfg, "r")
|
||||
loadSection(model, cfg, "p")
|
||||
loadSection(model, cfg, "e")
|
||||
loadSection(model, cfg, "m")
|
||||
|
||||
loadSection(model, cfg, "g")
|
||||
}
|
||||
|
||||
// LoadModelFromText loads the model from the text.
|
||||
func (model Model) LoadModelFromText(text string) {
|
||||
cfg, err := config.NewConfigFromText(text)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
|
||||
loadSection(model, cfg, "r")
|
||||
loadSection(model, cfg, "p")
|
||||
loadSection(model, cfg, "e")
|
||||
loadSection(model, cfg, "m")
|
||||
|
||||
loadSection(model, cfg, "g")
|
||||
}
|
||||
|
||||
// PrintModel prints the model to the log.
|
||||
func (model Model) PrintModel() {
|
||||
util.LogPrint("Model:")
|
||||
for k, v := range model {
|
||||
for i, j := range v {
|
||||
util.LogPrintf("%s.%s: %s", k, i, j.Value)
|
||||
}
|
||||
}
|
||||
}
|
||||
146
vendor/github.com/casbin/casbin/model/policy.go
generated
vendored
Normal file
146
vendor/github.com/casbin/casbin/model/policy.go
generated
vendored
Normal file
@@ -0,0 +1,146 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package model
|
||||
|
||||
import (
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// BuildRoleLinks initializes the roles in RBAC.
|
||||
func (model Model) BuildRoleLinks(rm rbac.RoleManager) {
|
||||
for _, ast := range model["g"] {
|
||||
ast.buildRoleLinks(rm)
|
||||
}
|
||||
}
|
||||
|
||||
// PrintPolicy prints the policy to log.
|
||||
func (model Model) PrintPolicy() {
|
||||
util.LogPrint("Policy:")
|
||||
for key, ast := range model["p"] {
|
||||
util.LogPrint(key, ": ", ast.Value, ": ", ast.Policy)
|
||||
}
|
||||
|
||||
for key, ast := range model["g"] {
|
||||
util.LogPrint(key, ": ", ast.Value, ": ", ast.Policy)
|
||||
}
|
||||
}
|
||||
|
||||
// ClearPolicy clears all current policy.
|
||||
func (model Model) ClearPolicy() {
|
||||
for _, ast := range model["p"] {
|
||||
ast.Policy = nil
|
||||
}
|
||||
|
||||
for _, ast := range model["g"] {
|
||||
ast.Policy = nil
|
||||
}
|
||||
}
|
||||
|
||||
// GetPolicy gets all rules in a policy.
|
||||
func (model Model) GetPolicy(sec string, ptype string) [][]string {
|
||||
return model[sec][ptype].Policy
|
||||
}
|
||||
|
||||
// GetFilteredPolicy gets rules based on field filters from a policy.
|
||||
func (model Model) GetFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) [][]string {
|
||||
res := [][]string{}
|
||||
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
matched := true
|
||||
for i, fieldValue := range fieldValues {
|
||||
if fieldValue != "" && rule[fieldIndex+i] != fieldValue {
|
||||
matched = false
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if matched {
|
||||
res = append(res, rule)
|
||||
}
|
||||
}
|
||||
|
||||
return res
|
||||
}
|
||||
|
||||
// HasPolicy determines whether a model has the specified policy rule.
|
||||
func (model Model) HasPolicy(sec string, ptype string, rule []string) bool {
|
||||
for _, r := range model[sec][ptype].Policy {
|
||||
if util.ArrayEquals(rule, r) {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the model.
|
||||
func (model Model) AddPolicy(sec string, ptype string, rule []string) bool {
|
||||
if !model.HasPolicy(sec, ptype, rule) {
|
||||
model[sec][ptype].Policy = append(model[sec][ptype].Policy, rule)
|
||||
return true
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the model.
|
||||
func (model Model) RemovePolicy(sec string, ptype string, rule []string) bool {
|
||||
for i, r := range model[sec][ptype].Policy {
|
||||
if util.ArrayEquals(rule, r) {
|
||||
model[sec][ptype].Policy = append(model[sec][ptype].Policy[:i], model[sec][ptype].Policy[i+1:]...)
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules based on field filters from the model.
|
||||
func (model Model) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) bool {
|
||||
tmp := [][]string{}
|
||||
res := false
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
matched := true
|
||||
for i, fieldValue := range fieldValues {
|
||||
if fieldValue != "" && rule[fieldIndex+i] != fieldValue {
|
||||
matched = false
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
if matched {
|
||||
res = true
|
||||
} else {
|
||||
tmp = append(tmp, rule)
|
||||
}
|
||||
}
|
||||
|
||||
model[sec][ptype].Policy = tmp
|
||||
return res
|
||||
}
|
||||
|
||||
// GetValuesForFieldInPolicy gets all values for a field for all rules in a policy, duplicated values are removed.
|
||||
func (model Model) GetValuesForFieldInPolicy(sec string, ptype string, fieldIndex int) []string {
|
||||
values := []string{}
|
||||
|
||||
for _, rule := range model[sec][ptype].Policy {
|
||||
values = append(values, rule[fieldIndex])
|
||||
}
|
||||
|
||||
util.ArrayRemoveDuplicates(&values)
|
||||
// sort.Strings(values)
|
||||
|
||||
return values
|
||||
}
|
||||
56
vendor/github.com/casbin/casbin/persist/adapter.go
generated
vendored
Normal file
56
vendor/github.com/casbin/casbin/persist/adapter.go
generated
vendored
Normal file
@@ -0,0 +1,56 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
import (
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
)
|
||||
|
||||
// LoadPolicyLine loads a text line as a policy rule to model.
|
||||
func LoadPolicyLine(line string, model model.Model) {
|
||||
if line == "" {
|
||||
return
|
||||
}
|
||||
|
||||
if strings.HasPrefix(line, "#") {
|
||||
return
|
||||
}
|
||||
|
||||
tokens := strings.Split(line, ", ")
|
||||
|
||||
key := tokens[0]
|
||||
sec := key[:1]
|
||||
model[sec][key].Policy = append(model[sec][key].Policy, tokens[1:])
|
||||
}
|
||||
|
||||
// Adapter is the interface for Casbin adapters.
|
||||
type Adapter interface {
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
LoadPolicy(model model.Model) error
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
SavePolicy(model model.Model) error
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
AddPolicy(sec string, ptype string, rule []string) error
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
RemovePolicy(sec string, ptype string, rule []string) error
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
// This is part of the Auto-Save feature.
|
||||
RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error
|
||||
}
|
||||
29
vendor/github.com/casbin/casbin/persist/adapter_filtered.go
generated
vendored
Normal file
29
vendor/github.com/casbin/casbin/persist/adapter_filtered.go
generated
vendored
Normal file
@@ -0,0 +1,29 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
import (
|
||||
"github.com/casbin/casbin/model"
|
||||
)
|
||||
|
||||
// FilteredAdapter is the interface for Casbin adapters supporting filtered policies.
|
||||
type FilteredAdapter interface {
|
||||
Adapter
|
||||
|
||||
// LoadFilteredPolicy loads only policy rules that match the filter.
|
||||
LoadFilteredPolicy(model model.Model, filter interface{}) error
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
IsFiltered() bool
|
||||
}
|
||||
117
vendor/github.com/casbin/casbin/persist/file-adapter/adapter.go
generated
vendored
Normal file
117
vendor/github.com/casbin/casbin/persist/file-adapter/adapter.go
generated
vendored
Normal file
@@ -0,0 +1,117 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"bytes"
|
||||
"errors"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// Adapter is the file adapter for Casbin.
|
||||
// It can load policy from file or save policy to file.
|
||||
type Adapter struct {
|
||||
filePath string
|
||||
}
|
||||
|
||||
// NewAdapter is the constructor for Adapter.
|
||||
func NewAdapter(filePath string) *Adapter {
|
||||
return &Adapter{filePath: filePath}
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *Adapter) LoadPolicy(model model.Model) error {
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
return a.loadPolicyFile(model, persist.LoadPolicyLine)
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *Adapter) SavePolicy(model model.Model) error {
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
var tmp bytes.Buffer
|
||||
|
||||
for ptype, ast := range model["p"] {
|
||||
for _, rule := range ast.Policy {
|
||||
tmp.WriteString(ptype + ", ")
|
||||
tmp.WriteString(util.ArrayToString(rule))
|
||||
tmp.WriteString("\n")
|
||||
}
|
||||
}
|
||||
|
||||
for ptype, ast := range model["g"] {
|
||||
for _, rule := range ast.Policy {
|
||||
tmp.WriteString(ptype + ", ")
|
||||
tmp.WriteString(util.ArrayToString(rule))
|
||||
tmp.WriteString("\n")
|
||||
}
|
||||
}
|
||||
|
||||
return a.savePolicyFile(strings.TrimRight(tmp.String(), "\n"))
|
||||
}
|
||||
|
||||
func (a *Adapter) loadPolicyFile(model model.Model, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
scanner := bufio.NewScanner(f)
|
||||
for scanner.Scan() {
|
||||
line := strings.TrimSpace(scanner.Text())
|
||||
handler(line, model)
|
||||
}
|
||||
return scanner.Err()
|
||||
}
|
||||
|
||||
func (a *Adapter) savePolicyFile(text string) error {
|
||||
f, err := os.Create(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
w := bufio.NewWriter(f)
|
||||
// error intentionally ignored
|
||||
w.WriteString(text)
|
||||
w.Flush()
|
||||
f.Close()
|
||||
return nil
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
func (a *Adapter) AddPolicy(sec string, ptype string, rule []string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
func (a *Adapter) RemovePolicy(sec string, ptype string, rule []string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
func (a *Adapter) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error {
|
||||
return errors.New("not implemented")
|
||||
}
|
||||
137
vendor/github.com/casbin/casbin/persist/file-adapter/adapter_filtered.go
generated
vendored
Normal file
137
vendor/github.com/casbin/casbin/persist/file-adapter/adapter_filtered.go
generated
vendored
Normal file
@@ -0,0 +1,137 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"errors"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// FilteredAdapter is the filtered file adapter for Casbin. It can load policy
|
||||
// from file or save policy to file and supports loading of filtered policies.
|
||||
type FilteredAdapter struct {
|
||||
*Adapter
|
||||
filtered bool
|
||||
}
|
||||
|
||||
// Filter defines the filtering rules for a FilteredAdapter's policy. Empty values
|
||||
// are ignored, but all others must match the filter.
|
||||
type Filter struct {
|
||||
P []string
|
||||
G []string
|
||||
}
|
||||
|
||||
// NewFilteredAdapter is the constructor for FilteredAdapter.
|
||||
func NewFilteredAdapter(filePath string) *FilteredAdapter {
|
||||
a := FilteredAdapter{}
|
||||
a.Adapter = NewAdapter(filePath)
|
||||
return &a
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *FilteredAdapter) LoadPolicy(model model.Model) error {
|
||||
a.filtered = false
|
||||
return a.Adapter.LoadPolicy(model)
|
||||
}
|
||||
|
||||
// LoadFilteredPolicy loads only policy rules that match the filter.
|
||||
func (a *FilteredAdapter) LoadFilteredPolicy(model model.Model, filter interface{}) error {
|
||||
if filter == nil {
|
||||
return a.LoadPolicy(model)
|
||||
}
|
||||
if a.filePath == "" {
|
||||
return errors.New("invalid file path, file path cannot be empty")
|
||||
}
|
||||
|
||||
filterValue, ok := filter.(*Filter)
|
||||
if !ok {
|
||||
return errors.New("invalid filter type")
|
||||
}
|
||||
err := a.loadFilteredPolicyFile(model, filterValue, persist.LoadPolicyLine)
|
||||
if err == nil {
|
||||
a.filtered = true
|
||||
}
|
||||
return err
|
||||
}
|
||||
|
||||
func (a *FilteredAdapter) loadFilteredPolicyFile(model model.Model, filter *Filter, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
scanner := bufio.NewScanner(f)
|
||||
for scanner.Scan() {
|
||||
line := strings.TrimSpace(scanner.Text())
|
||||
|
||||
if filterLine(line, filter) {
|
||||
continue
|
||||
}
|
||||
|
||||
handler(line, model)
|
||||
}
|
||||
return scanner.Err()
|
||||
}
|
||||
|
||||
// IsFiltered returns true if the loaded policy has been filtered.
|
||||
func (a *FilteredAdapter) IsFiltered() bool {
|
||||
return a.filtered
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *FilteredAdapter) SavePolicy(model model.Model) error {
|
||||
if a.filtered {
|
||||
return errors.New("cannot save a filtered policy")
|
||||
}
|
||||
return a.Adapter.SavePolicy(model)
|
||||
}
|
||||
|
||||
func filterLine(line string, filter *Filter) bool {
|
||||
if filter == nil {
|
||||
return false
|
||||
}
|
||||
p := strings.Split(line, ",")
|
||||
if len(p) == 0 {
|
||||
return true
|
||||
}
|
||||
var filterSlice []string
|
||||
switch strings.TrimSpace(p[0]) {
|
||||
case "p":
|
||||
filterSlice = filter.P
|
||||
case "g":
|
||||
filterSlice = filter.G
|
||||
}
|
||||
return filterWords(p, filterSlice)
|
||||
}
|
||||
|
||||
func filterWords(line []string, filter []string) bool {
|
||||
if len(line) < len(filter)+1 {
|
||||
return true
|
||||
}
|
||||
var skipLine bool
|
||||
for i, v := range filter {
|
||||
if len(v) > 0 && strings.TrimSpace(v) != strings.TrimSpace(line[i+1]) {
|
||||
skipLine = true
|
||||
break
|
||||
}
|
||||
}
|
||||
return skipLine
|
||||
}
|
||||
100
vendor/github.com/casbin/casbin/persist/file-adapter/adapter_mock.go
generated
vendored
Normal file
100
vendor/github.com/casbin/casbin/persist/file-adapter/adapter_mock.go
generated
vendored
Normal file
@@ -0,0 +1,100 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package fileadapter
|
||||
|
||||
import (
|
||||
"bufio"
|
||||
"errors"
|
||||
"io"
|
||||
"os"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/model"
|
||||
"github.com/casbin/casbin/persist"
|
||||
)
|
||||
|
||||
// AdapterMock is the file adapter for Casbin.
|
||||
// It can load policy from file or save policy to file.
|
||||
type AdapterMock struct {
|
||||
filePath string
|
||||
errorValue string
|
||||
}
|
||||
|
||||
// NewAdapterMock is the constructor for AdapterMock.
|
||||
func NewAdapterMock(filePath string) *AdapterMock {
|
||||
a := AdapterMock{}
|
||||
a.filePath = filePath
|
||||
return &a
|
||||
}
|
||||
|
||||
// LoadPolicy loads all policy rules from the storage.
|
||||
func (a *AdapterMock) LoadPolicy(model model.Model) error {
|
||||
err := a.loadPolicyFile(model, persist.LoadPolicyLine)
|
||||
return err
|
||||
}
|
||||
|
||||
// SavePolicy saves all policy rules to the storage.
|
||||
func (a *AdapterMock) SavePolicy(model model.Model) error {
|
||||
return nil
|
||||
}
|
||||
|
||||
func (a *AdapterMock) loadPolicyFile(model model.Model, handler func(string, model.Model)) error {
|
||||
f, err := os.Open(a.filePath)
|
||||
if err != nil {
|
||||
return err
|
||||
}
|
||||
defer f.Close()
|
||||
|
||||
buf := bufio.NewReader(f)
|
||||
for {
|
||||
line, err := buf.ReadString('\n')
|
||||
line = strings.TrimSpace(line)
|
||||
handler(line, model)
|
||||
if err != nil {
|
||||
if err == io.EOF {
|
||||
return nil
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
// SetMockErr sets string to be returned by of the mock during testing
|
||||
func (a *AdapterMock) SetMockErr(errorToSet string) {
|
||||
a.errorValue = errorToSet
|
||||
}
|
||||
|
||||
// GetMockErr returns a mock error or nil
|
||||
func (a *AdapterMock) GetMockErr() error {
|
||||
var returnError error
|
||||
if a.errorValue != "" {
|
||||
returnError = errors.New(a.errorValue)
|
||||
}
|
||||
return returnError
|
||||
}
|
||||
|
||||
// AddPolicy adds a policy rule to the storage.
|
||||
func (a *AdapterMock) AddPolicy(sec string, ptype string, rule []string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
|
||||
// RemovePolicy removes a policy rule from the storage.
|
||||
func (a *AdapterMock) RemovePolicy(sec string, ptype string, rule []string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
|
||||
// RemoveFilteredPolicy removes policy rules that match the filter from the storage.
|
||||
func (a *AdapterMock) RemoveFilteredPolicy(sec string, ptype string, fieldIndex int, fieldValues ...string) error {
|
||||
return a.GetMockErr()
|
||||
}
|
||||
27
vendor/github.com/casbin/casbin/persist/watcher.go
generated
vendored
Normal file
27
vendor/github.com/casbin/casbin/persist/watcher.go
generated
vendored
Normal file
@@ -0,0 +1,27 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package persist
|
||||
|
||||
// Watcher is the interface for Casbin watchers.
|
||||
type Watcher interface {
|
||||
// SetUpdateCallback sets the callback function that the watcher will call
|
||||
// when the policy in DB has been changed by other instances.
|
||||
// A classic callback is Enforcer.LoadPolicy().
|
||||
SetUpdateCallback(func(string)) error
|
||||
// Update calls the update callback of other instances to synchronize their policy.
|
||||
// It is usually called after changing the policy in DB, like Enforcer.SavePolicy(),
|
||||
// Enforcer.AddPolicy(), Enforcer.RemovePolicy(), etc.
|
||||
Update() error
|
||||
}
|
||||
257
vendor/github.com/casbin/casbin/rbac/default-role-manager/role_manager.go
generated
vendored
Normal file
257
vendor/github.com/casbin/casbin/rbac/default-role-manager/role_manager.go
generated
vendored
Normal file
@@ -0,0 +1,257 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package defaultrolemanager
|
||||
|
||||
import (
|
||||
"errors"
|
||||
"sync"
|
||||
|
||||
"github.com/casbin/casbin/rbac"
|
||||
"github.com/casbin/casbin/util"
|
||||
)
|
||||
|
||||
// RoleManager provides a default implementation for the RoleManager interface
|
||||
type RoleManager struct {
|
||||
allRoles *sync.Map
|
||||
maxHierarchyLevel int
|
||||
}
|
||||
|
||||
// NewRoleManager is the constructor for creating an instance of the
|
||||
// default RoleManager implementation.
|
||||
func NewRoleManager(maxHierarchyLevel int) rbac.RoleManager {
|
||||
rm := RoleManager{}
|
||||
rm.allRoles = &sync.Map{}
|
||||
rm.maxHierarchyLevel = maxHierarchyLevel
|
||||
return &rm
|
||||
}
|
||||
|
||||
func (rm *RoleManager) hasRole(name string) bool {
|
||||
_, ok := rm.allRoles.Load(name)
|
||||
return ok
|
||||
}
|
||||
|
||||
func (rm *RoleManager) createRole(name string) *Role {
|
||||
role, _ := rm.allRoles.LoadOrStore(name, newRole(name))
|
||||
return role.(*Role)
|
||||
}
|
||||
|
||||
// Clear clears all stored data and resets the role manager to the initial state.
|
||||
func (rm *RoleManager) Clear() error {
|
||||
rm.allRoles = &sync.Map{}
|
||||
return nil
|
||||
}
|
||||
|
||||
// AddLink adds the inheritance link between role: name1 and role: name2.
|
||||
// aka role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) AddLink(name1 string, name2 string, domain ...string) error {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
role2 := rm.createRole(name2)
|
||||
role1.addRole(role2)
|
||||
return nil
|
||||
}
|
||||
|
||||
// DeleteLink deletes the inheritance link between role: name1 and role: name2.
|
||||
// aka role: name1 does not inherit role: name2 any more.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) DeleteLink(name1 string, name2 string, domain ...string) error {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if !rm.hasRole(name1) || !rm.hasRole(name2) {
|
||||
return errors.New("error: name1 or name2 does not exist")
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
role2 := rm.createRole(name2)
|
||||
role1.deleteRole(role2)
|
||||
return nil
|
||||
}
|
||||
|
||||
// HasLink determines whether role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) HasLink(name1 string, name2 string, domain ...string) (bool, error) {
|
||||
if len(domain) == 1 {
|
||||
name1 = domain[0] + "::" + name1
|
||||
name2 = domain[0] + "::" + name2
|
||||
} else if len(domain) > 1 {
|
||||
return false, errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if name1 == name2 {
|
||||
return true, nil
|
||||
}
|
||||
|
||||
if !rm.hasRole(name1) || !rm.hasRole(name2) {
|
||||
return false, nil
|
||||
}
|
||||
|
||||
role1 := rm.createRole(name1)
|
||||
return role1.hasRole(name2, rm.maxHierarchyLevel), nil
|
||||
}
|
||||
|
||||
// GetRoles gets the roles that a subject inherits.
|
||||
// domain is a prefix to the roles.
|
||||
func (rm *RoleManager) GetRoles(name string, domain ...string) ([]string, error) {
|
||||
if len(domain) == 1 {
|
||||
name = domain[0] + "::" + name
|
||||
} else if len(domain) > 1 {
|
||||
return nil, errors.New("error: domain should be 1 parameter")
|
||||
}
|
||||
|
||||
if !rm.hasRole(name) {
|
||||
return nil, errors.New("error: name does not exist")
|
||||
}
|
||||
|
||||
roles := rm.createRole(name).getRoles()
|
||||
if len(domain) == 1 {
|
||||
for i := range roles {
|
||||
roles[i] = roles[i][len(domain[0])+2:]
|
||||
}
|
||||
}
|
||||
return roles, nil
|
||||
}
|
||||
|
||||
// GetUsers gets the users that inherits a subject.
|
||||
// domain is an unreferenced parameter here, may be used in other implementations.
|
||||
func (rm *RoleManager) GetUsers(name string, domain ...string) ([]string, error) {
|
||||
if !rm.hasRole(name) {
|
||||
return nil, errors.New("error: name does not exist")
|
||||
}
|
||||
|
||||
names := []string{}
|
||||
rm.allRoles.Range(func(_, value interface{}) bool {
|
||||
role := value.(*Role)
|
||||
if role.hasDirectRole(name) {
|
||||
names = append(names, role.name)
|
||||
}
|
||||
return true
|
||||
})
|
||||
return names, nil
|
||||
}
|
||||
|
||||
// PrintRoles prints all the roles to log.
|
||||
func (rm *RoleManager) PrintRoles() error {
|
||||
line := ""
|
||||
rm.allRoles.Range(func(_, value interface{}) bool {
|
||||
if text := value.(*Role).toString(); text != "" {
|
||||
if line == "" {
|
||||
line = text
|
||||
} else {
|
||||
line += ", " + text
|
||||
}
|
||||
}
|
||||
return true
|
||||
})
|
||||
util.LogPrint(line)
|
||||
return nil
|
||||
}
|
||||
|
||||
// Role represents the data structure for a role in RBAC.
|
||||
type Role struct {
|
||||
name string
|
||||
roles []*Role
|
||||
}
|
||||
|
||||
func newRole(name string) *Role {
|
||||
r := Role{}
|
||||
r.name = name
|
||||
return &r
|
||||
}
|
||||
|
||||
func (r *Role) addRole(role *Role) {
|
||||
for _, rr := range r.roles {
|
||||
if rr.name == role.name {
|
||||
return
|
||||
}
|
||||
}
|
||||
|
||||
r.roles = append(r.roles, role)
|
||||
}
|
||||
|
||||
func (r *Role) deleteRole(role *Role) {
|
||||
for i, rr := range r.roles {
|
||||
if rr.name == role.name {
|
||||
r.roles = append(r.roles[:i], r.roles[i+1:]...)
|
||||
return
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
func (r *Role) hasRole(name string, hierarchyLevel int) bool {
|
||||
if r.name == name {
|
||||
return true
|
||||
}
|
||||
|
||||
if hierarchyLevel <= 0 {
|
||||
return false
|
||||
}
|
||||
|
||||
for _, role := range r.roles {
|
||||
if role.hasRole(name, hierarchyLevel-1) {
|
||||
return true
|
||||
}
|
||||
}
|
||||
return false
|
||||
}
|
||||
|
||||
func (r *Role) hasDirectRole(name string) bool {
|
||||
for _, role := range r.roles {
|
||||
if role.name == name {
|
||||
return true
|
||||
}
|
||||
}
|
||||
|
||||
return false
|
||||
}
|
||||
|
||||
func (r *Role) toString() string {
|
||||
names := ""
|
||||
if len(r.roles) == 0 {
|
||||
return ""
|
||||
}
|
||||
for i, role := range r.roles {
|
||||
if i == 0 {
|
||||
names += role.name
|
||||
} else {
|
||||
names += ", " + role.name
|
||||
}
|
||||
}
|
||||
|
||||
if len(r.roles) == 1 {
|
||||
return r.name + " < " + names
|
||||
} else {
|
||||
return r.name + " < (" + names + ")"
|
||||
}
|
||||
}
|
||||
|
||||
func (r *Role) getRoles() []string {
|
||||
names := []string{}
|
||||
for _, role := range r.roles {
|
||||
names = append(names, role.name)
|
||||
}
|
||||
return names
|
||||
}
|
||||
38
vendor/github.com/casbin/casbin/rbac/role_manager.go
generated
vendored
Normal file
38
vendor/github.com/casbin/casbin/rbac/role_manager.go
generated
vendored
Normal file
@@ -0,0 +1,38 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package rbac
|
||||
|
||||
// RoleManager provides interface to define the operations for managing roles.
|
||||
type RoleManager interface {
|
||||
// Clear clears all stored data and resets the role manager to the initial state.
|
||||
Clear() error
|
||||
// AddLink adds the inheritance link between two roles. role: name1 and role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
AddLink(name1 string, name2 string, domain ...string) error
|
||||
// DeleteLink deletes the inheritance link between two roles. role: name1 and role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
DeleteLink(name1 string, name2 string, domain ...string) error
|
||||
// HasLink determines whether a link exists between two roles. role: name1 inherits role: name2.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
HasLink(name1 string, name2 string, domain ...string) (bool, error)
|
||||
// GetRoles gets the roles that a user inherits.
|
||||
// domain is a prefix to the roles (can be used for other purposes).
|
||||
GetRoles(name string, domain ...string) ([]string, error)
|
||||
// GetUsers gets the users that inherits a role.
|
||||
// domain is a prefix to the users (can be used for other purposes).
|
||||
GetUsers(name string, domain ...string) ([]string, error)
|
||||
// PrintRoles prints all the roles to log.
|
||||
PrintRoles() error
|
||||
}
|
||||
127
vendor/github.com/casbin/casbin/rbac_api.go
generated
vendored
Normal file
127
vendor/github.com/casbin/casbin/rbac_api.go
generated
vendored
Normal file
@@ -0,0 +1,127 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUser gets the roles that a user has.
|
||||
func (e *Enforcer) GetRolesForUser(name string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetRoles(name)
|
||||
return res
|
||||
}
|
||||
|
||||
// GetUsersForRole gets the users that has a role.
|
||||
func (e *Enforcer) GetUsersForRole(name string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetUsers(name)
|
||||
return res
|
||||
}
|
||||
|
||||
// HasRoleForUser determines whether a user has a role.
|
||||
func (e *Enforcer) HasRoleForUser(name string, role string) bool {
|
||||
roles := e.GetRolesForUser(name)
|
||||
|
||||
hasRole := false
|
||||
for _, r := range roles {
|
||||
if r == role {
|
||||
hasRole = true
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
return hasRole
|
||||
}
|
||||
|
||||
// AddRoleForUser adds a role for a user.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *Enforcer) AddRoleForUser(user string, role string) bool {
|
||||
return e.AddGroupingPolicy(user, role)
|
||||
}
|
||||
|
||||
// DeleteRoleForUser deletes a role for a user.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *Enforcer) DeleteRoleForUser(user string, role string) bool {
|
||||
return e.RemoveGroupingPolicy(user, role)
|
||||
}
|
||||
|
||||
// DeleteRolesForUser deletes all roles for a user.
|
||||
// Returns false if the user does not have any roles (aka not affected).
|
||||
func (e *Enforcer) DeleteRolesForUser(user string) bool {
|
||||
return e.RemoveFilteredGroupingPolicy(0, user)
|
||||
}
|
||||
|
||||
// DeleteUser deletes a user.
|
||||
// Returns false if the user does not exist (aka not affected).
|
||||
func (e *Enforcer) DeleteUser(user string) bool {
|
||||
return e.RemoveFilteredGroupingPolicy(0, user)
|
||||
}
|
||||
|
||||
// DeleteRole deletes a role.
|
||||
func (e *Enforcer) DeleteRole(role string) {
|
||||
e.RemoveFilteredGroupingPolicy(1, role)
|
||||
e.RemoveFilteredPolicy(0, role)
|
||||
}
|
||||
|
||||
// DeletePermission deletes a permission.
|
||||
// Returns false if the permission does not exist (aka not affected).
|
||||
func (e *Enforcer) DeletePermission(permission ...string) bool {
|
||||
return e.RemoveFilteredPolicy(1, permission...)
|
||||
}
|
||||
|
||||
// AddPermissionForUser adds a permission for a user or role.
|
||||
// Returns false if the user or role already has the permission (aka not affected).
|
||||
func (e *Enforcer) AddPermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.AddPolicy(params...)
|
||||
}
|
||||
|
||||
// DeletePermissionForUser deletes a permission for a user or role.
|
||||
// Returns false if the user or role does not have the permission (aka not affected).
|
||||
func (e *Enforcer) DeletePermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.RemovePolicy(params...)
|
||||
}
|
||||
|
||||
// DeletePermissionsForUser deletes permissions for a user or role.
|
||||
// Returns false if the user or role does not have any permissions (aka not affected).
|
||||
func (e *Enforcer) DeletePermissionsForUser(user string) bool {
|
||||
return e.RemoveFilteredPolicy(0, user)
|
||||
}
|
||||
|
||||
// GetPermissionsForUser gets permissions for a user or role.
|
||||
func (e *Enforcer) GetPermissionsForUser(user string) [][]string {
|
||||
return e.GetFilteredPolicy(0, user)
|
||||
}
|
||||
|
||||
// HasPermissionForUser determines whether a user has a permission.
|
||||
func (e *Enforcer) HasPermissionForUser(user string, permission ...string) bool {
|
||||
params := make([]interface{}, 0, len(permission)+1)
|
||||
|
||||
params = append(params, user)
|
||||
for _, perm := range permission {
|
||||
params = append(params, perm)
|
||||
}
|
||||
|
||||
return e.HasPolicy(params...)
|
||||
}
|
||||
121
vendor/github.com/casbin/casbin/rbac_api_synced.go
generated
vendored
Normal file
121
vendor/github.com/casbin/casbin/rbac_api_synced.go
generated
vendored
Normal file
@@ -0,0 +1,121 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUser gets the roles that a user has.
|
||||
func (e *SyncedEnforcer) GetRolesForUser(name string) []string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetRolesForUser(name)
|
||||
}
|
||||
|
||||
// GetUsersForRole gets the users that has a role.
|
||||
func (e *SyncedEnforcer) GetUsersForRole(name string) []string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetUsersForRole(name)
|
||||
}
|
||||
|
||||
// HasRoleForUser determines whether a user has a role.
|
||||
func (e *SyncedEnforcer) HasRoleForUser(name string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.HasRoleForUser(name, role)
|
||||
}
|
||||
|
||||
// AddRoleForUser adds a role for a user.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *SyncedEnforcer) AddRoleForUser(user string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddRoleForUser(user, role)
|
||||
}
|
||||
|
||||
// DeleteRoleForUser deletes a role for a user.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteRoleForUser(user string, role string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteRoleForUser(user, role)
|
||||
}
|
||||
|
||||
// DeleteRolesForUser deletes all roles for a user.
|
||||
// Returns false if the user does not have any roles (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteRolesForUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteRolesForUser(user)
|
||||
}
|
||||
|
||||
// DeleteUser deletes a user.
|
||||
// Returns false if the user does not exist (aka not affected).
|
||||
func (e *SyncedEnforcer) DeleteUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeleteUser(user)
|
||||
}
|
||||
|
||||
// DeleteRole deletes a role.
|
||||
func (e *SyncedEnforcer) DeleteRole(role string) {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
e.Enforcer.DeleteRole(role)
|
||||
}
|
||||
|
||||
// DeletePermission deletes a permission.
|
||||
// Returns false if the permission does not exist (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermission(permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermission(permission...)
|
||||
}
|
||||
|
||||
// AddPermissionForUser adds a permission for a user or role.
|
||||
// Returns false if the user or role already has the permission (aka not affected).
|
||||
func (e *SyncedEnforcer) AddPermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.AddPermissionForUser(user, permission...)
|
||||
}
|
||||
|
||||
// DeletePermissionForUser deletes a permission for a user or role.
|
||||
// Returns false if the user or role does not have the permission (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermissionForUser(user, permission...)
|
||||
}
|
||||
|
||||
// DeletePermissionsForUser deletes permissions for a user or role.
|
||||
// Returns false if the user or role does not have any permissions (aka not affected).
|
||||
func (e *SyncedEnforcer) DeletePermissionsForUser(user string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.DeletePermissionsForUser(user)
|
||||
}
|
||||
|
||||
// GetPermissionsForUser gets permissions for a user or role.
|
||||
func (e *SyncedEnforcer) GetPermissionsForUser(user string) [][]string {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.GetPermissionsForUser(user)
|
||||
}
|
||||
|
||||
// HasPermissionForUser determines whether a user has a permission.
|
||||
func (e *SyncedEnforcer) HasPermissionForUser(user string, permission ...string) bool {
|
||||
e.m.Lock()
|
||||
defer e.m.Unlock()
|
||||
return e.Enforcer.HasPermissionForUser(user, permission...)
|
||||
}
|
||||
38
vendor/github.com/casbin/casbin/rbac_api_with_domains.go
generated
vendored
Normal file
38
vendor/github.com/casbin/casbin/rbac_api_with_domains.go
generated
vendored
Normal file
@@ -0,0 +1,38 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package casbin
|
||||
|
||||
// GetRolesForUserInDomain gets the roles that a user has inside a domain.
|
||||
func (e *Enforcer) GetRolesForUserInDomain(name string, domain string) []string {
|
||||
res, _ := e.model["g"]["g"].RM.GetRoles(name, domain)
|
||||
return res
|
||||
}
|
||||
|
||||
// GetPermissionsForUserInDomain gets permissions for a user or role inside a domain.
|
||||
func (e *Enforcer) GetPermissionsForUserInDomain(user string, domain string) [][]string {
|
||||
return e.GetFilteredPolicy(0, user, domain)
|
||||
}
|
||||
|
||||
// AddRoleForUserInDomain adds a role for a user inside a domain.
|
||||
// Returns false if the user already has the role (aka not affected).
|
||||
func (e *Enforcer) AddRoleForUserInDomain(user string, role string, domain string) bool {
|
||||
return e.AddGroupingPolicy(user, role, domain)
|
||||
}
|
||||
|
||||
// DeleteRoleForUserInDomain deletes a role for a user inside a domain.
|
||||
// Returns false if the user does not have the role (aka not affected).
|
||||
func (e *Enforcer) DeleteRoleForUserInDomain(user string, role string, domain string) bool {
|
||||
return e.RemoveGroupingPolicy(user, role, domain)
|
||||
}
|
||||
160
vendor/github.com/casbin/casbin/util/builtin_operators.go
generated
vendored
Normal file
160
vendor/github.com/casbin/casbin/util/builtin_operators.go
generated
vendored
Normal file
@@ -0,0 +1,160 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package util
|
||||
|
||||
import (
|
||||
"net"
|
||||
"regexp"
|
||||
"strings"
|
||||
|
||||
"github.com/casbin/casbin/rbac"
|
||||
)
|
||||
|
||||
// KeyMatch determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*"
|
||||
func KeyMatch(key1 string, key2 string) bool {
|
||||
i := strings.Index(key2, "*")
|
||||
if i == -1 {
|
||||
return key1 == key2
|
||||
}
|
||||
|
||||
if len(key1) > i {
|
||||
return key1[:i] == key2[:i]
|
||||
}
|
||||
return key1 == key2[:i]
|
||||
}
|
||||
|
||||
// KeyMatchFunc is the wrapper for KeyMatch.
|
||||
func KeyMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return (bool)(KeyMatch(name1, name2)), nil
|
||||
}
|
||||
|
||||
// KeyMatch2 determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*", "/resource1" matches "/:resource"
|
||||
func KeyMatch2(key1 string, key2 string) bool {
|
||||
key2 = strings.Replace(key2, "/*", "/.*", -1)
|
||||
|
||||
re := regexp.MustCompile(`(.*):[^/]+(.*)`)
|
||||
for {
|
||||
if !strings.Contains(key2, "/:") {
|
||||
break
|
||||
}
|
||||
|
||||
key2 = "^" + re.ReplaceAllString(key2, "$1[^/]+$2") + "$"
|
||||
}
|
||||
|
||||
return RegexMatch(key1, key2)
|
||||
}
|
||||
|
||||
// KeyMatch2Func is the wrapper for KeyMatch2.
|
||||
func KeyMatch2Func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return (bool)(KeyMatch2(name1, name2)), nil
|
||||
}
|
||||
|
||||
// KeyMatch3 determines whether key1 matches the pattern of key2 (similar to RESTful path), key2 can contain a *.
|
||||
// For example, "/foo/bar" matches "/foo/*", "/resource1" matches "/{resource}"
|
||||
func KeyMatch3(key1 string, key2 string) bool {
|
||||
key2 = strings.Replace(key2, "/*", "/.*", -1)
|
||||
|
||||
re := regexp.MustCompile(`(.*)\{[^/]+\}(.*)`)
|
||||
for {
|
||||
if !strings.Contains(key2, "/{") {
|
||||
break
|
||||
}
|
||||
|
||||
key2 = re.ReplaceAllString(key2, "$1[^/]+$2")
|
||||
}
|
||||
|
||||
return RegexMatch(key1, key2)
|
||||
}
|
||||
|
||||
// KeyMatch3Func is the wrapper for KeyMatch3.
|
||||
func KeyMatch3Func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return (bool)(KeyMatch3(name1, name2)), nil
|
||||
}
|
||||
|
||||
// RegexMatch determines whether key1 matches the pattern of key2 in regular expression.
|
||||
func RegexMatch(key1 string, key2 string) bool {
|
||||
res, err := regexp.MatchString(key2, key1)
|
||||
if err != nil {
|
||||
panic(err)
|
||||
}
|
||||
return res
|
||||
}
|
||||
|
||||
// RegexMatchFunc is the wrapper for RegexMatch.
|
||||
func RegexMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
return (bool)(RegexMatch(name1, name2)), nil
|
||||
}
|
||||
|
||||
// IPMatch determines whether IP address ip1 matches the pattern of IP address ip2, ip2 can be an IP address or a CIDR pattern.
|
||||
// For example, "192.168.2.123" matches "192.168.2.0/24"
|
||||
func IPMatch(ip1 string, ip2 string) bool {
|
||||
objIP1 := net.ParseIP(ip1)
|
||||
if objIP1 == nil {
|
||||
panic("invalid argument: ip1 in IPMatch() function is not an IP address.")
|
||||
}
|
||||
|
||||
_, cidr, err := net.ParseCIDR(ip2)
|
||||
if err != nil {
|
||||
objIP2 := net.ParseIP(ip2)
|
||||
if objIP2 == nil {
|
||||
panic("invalid argument: ip2 in IPMatch() function is neither an IP address nor a CIDR.")
|
||||
}
|
||||
|
||||
return objIP1.Equal(objIP2)
|
||||
}
|
||||
|
||||
return cidr.Contains(objIP1)
|
||||
}
|
||||
|
||||
// IPMatchFunc is the wrapper for IPMatch.
|
||||
func IPMatchFunc(args ...interface{}) (interface{}, error) {
|
||||
ip1 := args[0].(string)
|
||||
ip2 := args[1].(string)
|
||||
|
||||
return (bool)(IPMatch(ip1, ip2)), nil
|
||||
}
|
||||
|
||||
// GenerateGFunction is the factory method of the g(_, _) function.
|
||||
func GenerateGFunction(rm rbac.RoleManager) func(args ...interface{}) (interface{}, error) {
|
||||
return func(args ...interface{}) (interface{}, error) {
|
||||
name1 := args[0].(string)
|
||||
name2 := args[1].(string)
|
||||
|
||||
if rm == nil {
|
||||
return name1 == name2, nil
|
||||
} else if len(args) == 2 {
|
||||
res, _ := rm.HasLink(name1, name2)
|
||||
return res, nil
|
||||
} else {
|
||||
domain := args[2].(string)
|
||||
res, _ := rm.HasLink(name1, name2, domain)
|
||||
return res, nil
|
||||
}
|
||||
}
|
||||
}
|
||||
34
vendor/github.com/casbin/casbin/util/log_util.go
generated
vendored
Normal file
34
vendor/github.com/casbin/casbin/util/log_util.go
generated
vendored
Normal file
@@ -0,0 +1,34 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package util
|
||||
|
||||
import "log"
|
||||
|
||||
// EnableLog controls whether to print log to console.
|
||||
var EnableLog = true
|
||||
|
||||
// LogPrint prints the log.
|
||||
func LogPrint(v ...interface{}) {
|
||||
if EnableLog {
|
||||
log.Print(v...)
|
||||
}
|
||||
}
|
||||
|
||||
// LogPrintf prints the log with the format.
|
||||
func LogPrintf(format string, v ...interface{}) {
|
||||
if EnableLog {
|
||||
log.Printf(format, v...)
|
||||
}
|
||||
}
|
||||
105
vendor/github.com/casbin/casbin/util/util.go
generated
vendored
Normal file
105
vendor/github.com/casbin/casbin/util/util.go
generated
vendored
Normal file
@@ -0,0 +1,105 @@
|
||||
// Copyright 2017 The casbin Authors. All Rights Reserved.
|
||||
//
|
||||
// Licensed under the Apache License, Version 2.0 (the "License");
|
||||
// you may not use this file except in compliance with the License.
|
||||
// You may obtain a copy of the License at
|
||||
//
|
||||
// http://www.apache.org/licenses/LICENSE-2.0
|
||||
//
|
||||
// Unless required by applicable law or agreed to in writing, software
|
||||
// distributed under the License is distributed on an "AS IS" BASIS,
|
||||
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
// See the License for the specific language governing permissions and
|
||||
// limitations under the License.
|
||||
|
||||
package util
|
||||
|
||||
import (
|
||||
"sort"
|
||||
"strings"
|
||||
)
|
||||
|
||||
// EscapeAssertion escapes the dots in the assertion, because the expression evaluation doesn't support such variable names.
|
||||
func EscapeAssertion(s string) string {
|
||||
s = strings.Replace(s, "r.", "r_", -1)
|
||||
s = strings.Replace(s, "p.", "p_", -1)
|
||||
return s
|
||||
}
|
||||
|
||||
// RemoveComments removes the comments starting with # in the text.
|
||||
func RemoveComments(s string) string {
|
||||
pos := strings.Index(s, "#")
|
||||
if pos == -1 {
|
||||
return s
|
||||
}
|
||||
return strings.TrimSpace(s[0:pos])
|
||||
}
|
||||
|
||||
// ArrayEquals determines whether two string arrays are identical.
|
||||
func ArrayEquals(a []string, b []string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
for i, v := range a {
|
||||
if v != b[i] {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
|
||||
// Array2DEquals determines whether two 2-dimensional string arrays are identical.
|
||||
func Array2DEquals(a [][]string, b [][]string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
for i, v := range a {
|
||||
if !ArrayEquals(v, b[i]) {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
|
||||
// ArrayRemoveDuplicates removes any duplicated elements in a string array.
|
||||
func ArrayRemoveDuplicates(s *[]string) {
|
||||
found := make(map[string]bool)
|
||||
j := 0
|
||||
for i, x := range *s {
|
||||
if !found[x] {
|
||||
found[x] = true
|
||||
(*s)[j] = (*s)[i]
|
||||
j++
|
||||
}
|
||||
}
|
||||
*s = (*s)[:j]
|
||||
}
|
||||
|
||||
// ArrayToString gets a printable string for a string array.
|
||||
func ArrayToString(s []string) string {
|
||||
return strings.Join(s, ", ")
|
||||
}
|
||||
|
||||
// ParamsToString gets a printable string for variable number of parameters.
|
||||
func ParamsToString(s ...string) string {
|
||||
return strings.Join(s, ", ")
|
||||
}
|
||||
|
||||
// SetEquals determines whether two string sets are identical.
|
||||
func SetEquals(a []string, b []string) bool {
|
||||
if len(a) != len(b) {
|
||||
return false
|
||||
}
|
||||
|
||||
sort.Strings(a)
|
||||
sort.Strings(b)
|
||||
|
||||
for i, v := range a {
|
||||
if v != b[i] {
|
||||
return false
|
||||
}
|
||||
}
|
||||
return true
|
||||
}
|
||||
Reference in New Issue
Block a user